 ?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
Image steganography and steganalysis, which involve concealing and uncovering hidden data within images, have gained significant attention in recent years, finding applications in various fields like military, medicine, e-government, and social media. Despite their importance in real-world applications, some practical aspects remain unaddressed. To bridge this gap, the current study compares image steganography and steganalysis tools and techniques for Digital Forensic Investigators (DFIs) to uncover concealed information in images. We perform a thorough review of Artificial Intelligence, statistical, and signature steganalysis methods, assesses both free and paid versions, and experiments with various image features like size, colour, mean square error (MSE), root mean square error (RMSE), and peak signal-to-noise ratio (PSNR) using a JPEG/PNG dataset. The research provides valuable insights for professionals in cybersecurity. The originality of this research resides in the fact that, although previous studies have been conducted in this area, none have explicitly examined the analysis of the selected tools—F5, Steghide, Outguess for image steganography, and Aletheia, StegExpose for image steganalysis—and their application to JPEG image analysis.
1. Introduction and related work
Steganography, a practice rooted in ancient history [Citation1], derives its name from the Greek term for ‘covert writing’, underlining its primary objective of concealing messages within alternative forms of media [Citation1]. Over time, steganography has evolved in numerous ways, from the creation of an astragal during the era of Aeneas the Tactician [Citation1] to its current manifestation [Citation2,Citation3], where the fundamental principle remains consistent: the concealment of messages within digital resources. The process of discovering the messages hidden inside the data payload is called steganalysis. The art of revealing hidden messages within data payloads is referred to as steganalysis, encompassing various techniques such as stego-only attacks, known cover attacks, known message attacks, and more [Citation4]. These techniques serve as invaluable tools for digital forensic investigators (DFI), in order to find hidden messages.
Over the past two decades of technological advancements, steganography has posed numerous challenges to cybersecurity specialists. This challenge includes detecting malicious data, embedded inside digital images, web advertisement banners, and videos [Citation5–7]. Most people would likely not suppose that an image or other digital resource received online contains hidden information or malware script. They will not be aware that this could corrupt their computer and even format their hard disk [Citation7]. For this reason, attention must be focused on steganography and detecting the presence of it.
DFI are among the professionals who are responsible for finding solutions to tackle the aforementioned challenges introduced by steganography. Their responsibilities include analyzing in detail computer programs and software, to obtain data from a damaged device, trace sources of a breach, or analyze electronic data [Citation8]. Multiple steganalysis techniques are employed to identify concealed messages within digital files, including signature-based, statistical, feature-based, deep learning (DL), and more [Citation9,Citation10]. Researchers have undertaken extensive comparisons of these techniques using various datasets, such as IStego100K [Citation11] and BOSS [Citation12], encompassing different categories of methods and technologies (AI, signature, or statistical) [Citation4,Citation10,Citation13–15].
Numerous research efforts [Citation4,Citation9,Citation10,Citation14,Citation16–19] have delved into the realms of image steganography and steganalysis. In 2011, Mayra and Frank [Citation16] conducted an insightful analysis of the key techniques and methods employed by forensic investigators in image steganography and steganalysis. Their work provided an extensive comparative evaluation of image steganography techniques, encompassing both transform and spatial domain-based approaches, and steganalysis techniques, including visual, and statistical measures. However, the authors indicated that there is always a room for better techniques and software for steganalysis to protect the important information. Further, in the year 2022, Mandal et al. [Citation18] conducted an extensive state-of-the-art review on digital image steganography, examining recent steganographic techniques and tools. They delved into discussions on deep learning-based steganographic techniques and the associated challenges. According to their findings, the primary challenge in proposing a steganographic technique lies in achieving a suitable balance between higher embedding capacity, imperceptibility, and security, thereby distinguishing it from related systems such as cryptography and watermarking. The authors recommended the incorporation of optimization techniques to enhance perceptibility. Additionally, they advocated for giving due consideration to hybrid techniques that combine both spatial domain and transform domain approaches. The authors also highlighted Quantum steganography and GAN-based steganography as emerging research directions worth focusing on.
Further, a study performed by Sarmah and Kulkarni [Citation20], concentrates on improving the existing Cohort Intelligence (CI) optimization algorithm. The improved version, when applied to JPEG image steganography, shows interesting and exciting results. It not only reduces computational costs compared to the original CI method but also demonstrates satisfactory image quality improvements. However, there were still certain challenges identified with respect to security. In addition, Johnson and Sushil [Citation21] presented the foundational work of a tool designed to automatically identify the presence of concealed messages in images. They examined several tools, including S-Tool, Hide and Seek, Hide4PGP, and Jsteg-Jpeg. According to their perspective, emphasis should be placed on the idea that if information is embedded within a cover in a way that is imperceptible to humans, then imperceptible alterations can be made to the cover, effectively erasing the embedded information. Also, there is an open door to discuss the steganalysis challenges considering these tools.
Furthermore, in 2021, Sharma et al. [Citation19] explored various methods of utilizing image steganography for safeguarding data transfer. In line with the work of the authors [Citation18], this paper concentrated on diverse techniques, including Least-significant bit (LSB) insertion, Discrete Cosine Transformation (DCT), Masking and Filtering, and the Scatter and Encrypt method. The comparative analysis of similar studies was also presented, outlining the pros and cons of the employed techniques. The authors recommended the creation of distinct image steganography approaches through amalgamations, repetitions, and modifications of existing methods, aiming to strike a balance between embedding capacity, image quality, and security.
In 2019, Chutani and Goyal [Citation14] conducted a review of crucial forensic methodologies for digital image steganalysis, as documented in the steganalysis literature. The authors delved into a discussion on important performance metrics and evaluation parameters accessible to steganalysts in their research, including payload estimation, multi-class classification, and stego key determination. Structural attacks and machine-learning-based attacks were also explored, with a focus on recent challenges faced by an ideal steganalyzer. Similarly, a paper by Nissar and Mir [Citation9] focuses on the classification of the existing steganalysis techniques. They indicate with respect to the best circumstances in which certain categories (signature, statistical) of techniques should be utilized. A study by Karampidis et al. [Citation4] also focuses on the existing image steganalysis methods and techniques. The paper compares visual, statistical, spread spectrum, and universal methods used in image steganalysis. It provides insight suggesting the appropriate usage of some of the aforementioned methods, depending on the information available to the DFI. For instance, in case only the stego object is known, then a statistical image steganalysis technique might be the most beneficial. Nevertheless, the main conclusion from the paper indicates that currently, it is impossible to utilize an image steganalysis algorithm with low computational needs and high accuracy.
The authors of [Citation22] conducted a review focusing on the most widely used datasets for image steganalysis, considering both spatial and transform domains, and employing classical machine learning as well as deep learning approaches. They categorized their dataset based on grayscale, colored, and a combination of both types of images. The authors emphasized the challenges present in contemporary steganalysis approaches, noting a significant issue being the absence of a generalized Convolutional Neural Network (CNN) model capable of detecting hidden messages in previously unseen data. Additionally, they pointed out that none of the existing deep learning models currently take into consideration the utilization of generative adversarial networks (GANs). Furthermore, numerous datasets are available with varying specifications, such as the data domain, yet the current deep learning models for steganalysis are adapted to specific datasets.
On the other side, Farooq and Selwal [Citation10] depict the current trends in artificial intelligence (AI) and provide a systematic review of the application of deep learning principles in image steganalysis. They achieve this by presenting a comparative analysis of existing deep learning-based methods and algorithms in both the spatial and frequency domains. The authors also examine evaluation metrics for assessing the performance of image steganalysis approaches, including quantitative metrics and visual metrics. Their study explores noteworthy open-source tools, such as Virtual Steganographic Laboratory (VSL), StegoSpy, Stegdetect, StegBreak, StegoSuite, and Ben-4D. The paper emphasizes the promising future of deep learning techniques in the field of image steganalysis. Selvaraj et al. [Citation23] also researched in a similar directions to propose the swift shift from traditional machine learning steganalysis approaches to deep learning approaches.
Giarimpampa’s research [Citation17] is dedicated to the evaluation of steganographic tools in both the transform and spatial domains, aiming to develop a blind image steganalysis method. The primary objective is to detect concealed messages within digital sources with the utmost precision and the lowest possible error rate. The study underscores the challenge of proving the efficacy of universal image steganalysis due to the absence of standardized scientific datasets. As a result, certain tools and algorithms exhibit high detection rates in the spatial domain but may not perform as effectively in the transform domain. This presents a significant hurdle in the creation of a completely definitive blind image steganalysis method for detecting steganography in images.
In 2018, Li et al. [Citation24] emphasized the importance of taking into account imaging factors such as ISO speed, exposure time, and noise level when applying an academic forensic tool to investigate real-world cases. The authors conducted experiments by collecting images with diverse exposure settings capturing the same scene content. Their research involved using iPhones and included over 1500 original TIFF images, generating 150 different scenes with identical exposure settings. The authors recommended adapting exposure parameters for target images, even on a fixed device, as this adjustment could notably enhance the performance of a forensic analyzer.
Upon a thorough review of the related literature on the topic of image steganography and steganalysis, it was evident that there were noticeable limitations in the existing techniques and tools. Not many studies have concentrated on explaining the merits and demerits of these existing steganalysis techniques. Therefore, a significant portion of the current research is dedicated to the exploration and discussion of the strengths and weaknesses inherent in current image steganalysis methods. The aim was to facilitate the work of DFI and serve as a road map indicating which approach or technique should be taken. Another limitation in the field of steganography and steganalysis constitutes the fact that not many papers compare the available forensic tools and their detection capabilities. Although, Provos and Honeman [Citation7] demonstrated the process for OpenStego, F5, and JSteg, however, they didn’t use any steganalysis tools or attacks except a distributed dictionary attack for image steganography.
This research provides an open avenue for researchers to identify and develop new tools for steganography and steganalysis to enhance existing outcomes. This is another niche area that was explored in the current study. The present study aims to conduct a comprehensive comparison of available steganography and steganalysis tools and techniques. Our goal is to provide valuable insights to DFI, especially regarding the JPEG format, which is one of the most used for image steganography [Citation25,Citation26]. We undertake a thorough examination of Artificial Intelligence, statistical, and signature steganalysis methods. Additionally, we evaluate both free and paid versions of existing image steganography and image steganalysis tools. Furthermore, we conduct experiments with widely-used non-paid steganography tools (F5 [Citation27], Steghide [Citation28], Outguess [Citation29]) and steganalysis tools (Aletheia [Citation30], StegExpose [Citation31]) using a JPEG/PNG dataset. Another interesting question in the domain of image steganography that could produce valuable results is, whether image features such as colour, size, peak signal-to-noise ratio (PSNR), mean square error (MSE), and root mean square error (RMSE), indicate the presence of hidden information.
2. Methodology
After discussing the context and related work on the topic of image steganography and steganalysis the current section focuses on the methodology. In this section, the different phases, identified in the experiment are explained and justified. Therefore, following the goal to help DFI in the field of digital image steganography and steganalysis, the following steps present the separate phases in the experiment:
Step 1: Perform a literature review on 2–3 steganalysis sub techniques (Preparation Phase).
Step 2: Evaluate whether AI-based techniques are more accurate than a signature and statistical ones (Preparation Phase).
Step 3: Construct a dataset of 30 JPEG images from Unsplash (Tool comparison Phase).
Step 4: Compare the detection accuracy of steganalysis tools Aletheia [Citation30] and StegExpose [Citation31] (Tool comparison Phase).
Step 5: Compare peak-signal-to-noise ratio (PSNR), mean square error (MSE), colour, and image size between stego and respective cover images Image feature analysis phase).
For the first two steps (Step 1 and Step 2) under Preparation Phase, a literature review was performed on 2–3 steganalysis sub-techniques from the AI, signature, or statistical domain. The papers for the literature review were found via a Google Scholar search, using ‘image steganalysis’, ‘steganalysis techniques’, ‘image steganography’, and ‘forensic’ key terms. The main goal was to identify, whether AI-related techniques produce more accurate results for detecting steganography inside digital images. The main metric of interest for the comparison process was the detection accuracy (in case it was present), obtained from the consulted papers during the literature reviews [Citation4,Citation32]. Furthermore, the general advantages and disadvantages of each category of techniques were also discussed.
Moving to the dataset tool comparison and image features analysis, several stages were followed in Step 3. The dataset, consisting of 30 random JPEG image files, obtained from Unsplash [Citation33], was composed of 15 colourful (RGB) and 15 grayscale (GS) that were identical to the colourful [Citation34], however, converted to grayscale with a free online tool called ImageOnline.co [Citation35]. Finally, all the images were resized to 512 × 512 dimensions with the ILoveIMG website [Citation36].
There were several reasons for choosing specifically JPEG images and composing a dataset of 30 images, rather than using an existing one like BOSS [Citation12]. For instance, most of the non-paid and widely used steganography and steganalysis tools work predominantly or exclusively with JPEG images. Furthermore, it is one of the most widely used image formats in the world [Citation37]. The decision to limit the dataset to just 30 images was primarily driven by time constraints. This choice was made in order to ensure a thorough analysis of each image using the three selected steganography tools and two steganalysis tools, as previously mentioned. The decision to set the image dimensions at 512 × 512 was made to assess the performance of all the steganography tools at a specific and widely employed image size. Regarding the concealment of messages, 5 text sizes (6 Bytes, 53 Bytes, 125 Bytes, 529 Bytes, and 1040 Bytes) were used to hide text inside 16 of the 30 images. The main idea was to analyse whether the detection accuracy is influenced by the embedded message size. Especially for 529 and 1040 Bytes, the focus was to identify whether surpassing the dimension threshold would influence significantly the exposure of the hidden message.
For the tool comparison phase (Step 4), using the above-mentioned dataset, 3 steganography tools for hiding information inside 16 images were utilized (most of the chosen cover images were more colourful and with bigger sizes in Bytes), with the remaining 14 being untouched. For detecting steganography inside the images, 2 steganalysis tools were used. For this research, Outguess [Citation38], F5 [Citation29], and StegHide [Citation27] were chosen as the steganography options for concealing messages. The 3 tools were one of the most popular non-paid and compatible with JPEG images [Citation32,Citation39]. After the construction of the dataset comprising both stego and non-stego images, we proceeded to the experimental phase. For the purpose of steganography detection in JPEG files, two widely recognized steganalysis tools were employed: Aletheia [Citation30] and StegExpose [Citation31]. The former offers a novel approach by implementing state-of-the-art machine learning techniques [Citation40], whereas the second is an older tool, yet, still currently used tool by DFI [Citation39].
In the actual experimental process, after acquiring the stego files for each image, both steganalysis tools were applied to the images to assess their accuracy. The accuracy was determined by summing the correctly identified stego images and correctly identified non-stego images and dividing this sum by the total number of images in the dataset (30). This approach was executed for each steganography tool and across various embedded hidden message sizes.
For the feature analysis phase (Step 5), given the stego images from the composed dataset, image features such as peak signal-to-noise ratio (PSNR), mean square error (MSE), colour and image size were analysed. They are widely used metrics for analysing images [Citation20]. The PSNR one measures the quality of the image between the original and changed image (stego image) in decibels (cover and stego images), with the following formula,
Where is the maximum pixel value of the image (8 for grayscale, 24 for RGB) [Citation39]. A higher PSNR indicates less distortion between the cover and stego images. However, it’s essential to note that a high PSNR doesn’t necessarily mean that the steganographic payload is invisible or undetectable, as it focuses on overall image quality rather than the perceptual impact of hidden information. MSE is an estimator, that measures the differences between 2 images (cover and stego). Using this formula,
where and
are the dimensions of the image,
,
are the individual pixel values from the cover and stego image, respectively [Citation41]. A lower MSE indicates better compression.
An effective steganographic method should aim to minimize the perceptual differences between the cover and stego images. MSE and PSNR provide a quantitative measure of these differences. On the other side, Steganalysis techniques may leverage MSE and PSNR to detect steganographic content by identifying images with unusually high MSE or low PSNR values compared to typical cover images. MSE and PSNR can also be used to indirectly estimate the embedding capacity of a steganographic method. If the method maintains a high PSNR despite embedding information, it suggests that the payload may be hidden more subtly or efficiently. While MSE and PSNR provide quantitative metrics, they do not fully capture human perceptual differences. A steganographic method may aim to keep these differences below the threshold of human perception, making the hidden information less detectable [Citation20].
To check the importance of the PSNR, MSE, and image size, several steps were taken. For each of the features, the mean and standard deviation (SD) values were computed, based on the stego images with different embedded messages. Both SD and mean were chosen, since they demonstrate how the stego image deviates from the cover image. This approach helps us investigate whether certain steganography tools introduce consistent alterations in the stego images or if these changes are detectable by digital forensic investigators (DFI) regardless of the tool used.
3. Results & discussion
In the following section the three phases (Preparation phase, Tool comparison phase, and Image feature analysis phase), identified in the Methodology section are discussed.
3.1. Preparation phase
The first phase of the experimentation was dedicated to the comparison of AI, signature, and statistical techniques used in steganalysis. The aim was to identify whether a certain category is more accurate in detecting steganography in digital images. To answer that, the preparation phase involved an extensive reviewing process on the available literature. The following studies [Citation4,Citation9,Citation10,Citation16,Citation22,Citation32,Citation42,Citation43] were examined and analysed, by observing the advantages, disadvantages, and use cases of techniques. From the above-referenced papers, a minimum of 2 and a maximum of 3 techniques from each domain (signature, statistical, and AI-based) were chosen. Moreover, a comparative analysis was conducted on image steganography and steganalysis tools to ascertain the availability of both free and paid options.
3.1.1. Signature-based
Signature steganalysis [Citation4] is a method, used by cybersecurity specialists, to search for steganography in digital images by observing repetitive patterns, introduced by common steganography tools. This could be done with the help of computer programs such as HxD that show the hexadecimal representation of the image. Previous research papers [Citation4,Citation9] have established that the presence of specific characters, often referred to as signatures, can serve as indicators that an image is a stego image, meaning it contains an embedded secret message.
For example, 5B 3B 31 53 00 is a common byte sequence embedded at the end of JPEG files (when the files are represented as sequences of bytes) that indicates the image might contain steganography [Citation4,Citation9]. Similarly”, CDN” appearing somewhere in the byte sequence representation of the image [Citation4,Citation43] can indicate that an image is stego. The selected 2 main sub-techniques from the signature domain, that are not AI-based, were specific signature steganalysis (SSS) [Citation9] and universal signature steganalysis (USS) [Citation9].
SSS is a technique, developed to tackle a concrete steganography algorithm, such as LSB and F5 [Citation44]. Some steganography algorithms may leave detectable traces, as highlighted in the preceding paragraph (5B 3B 31 53 00, CDN, etc.). Therefore, SSS algorithms provide the option to detect such traces, in case they are embedded in the stego file. Following that, the biggest limitation of the SSS methods is the required exact knowledge regarding which tool has been used. On the other side, USS focuses on identifying steganography in images, independent of the utilized algorithm for concealing the message. An example of such an algorithm has been proposed by Fridrich [Citation45]. It identifies steganography in JPEG images, by dividing the image into 8 × 8 blocks and extracting the quantization matrix from the discrete cosine transform (DCT) coefficients, which is compared with the standard JPEG quantization table. This technique has been tested and referenced as reliable, and capable of detecting hidden information even in case of flipping the LSB of one-pixel [Citation9]. Regarding the disadvantages, in case of re-scaling of the image, the JPEG signature may be lost [Citation9] and the algorithm only works on JPEG images [Citation4,Citation43].
During the review part of the existing studies, not enough information was found on the topic of detection accuracy in signature-based image steganalysis. However, from the consulted literature [Citation4,Citation9,Citation43] several conclusions can be made. In case the steganography tool leaves signature patterns, then signature-based steganalysis techniques, especially the specific ones, can produce decent results that signify the presence of steganography. For the universal ones, only the algorithm proposed by Friedrich [Citation45] was found to be useful, and very reliable, but it works solely in the JPEG domain. The following summarizes the findings of Signature sub-techniques.
Table 1. Signature sub-techniques overview.
Moreover, in their work from 2017, Hassan et al. [Citation46] delve into steganalysis tools designed for detecting concealed messages through signature analysis. The authors highlight Backbone Security’s steganography application fingerprint database (SAFDB) [Citation47], which encompasses signatures of 1050 steganography applications. This database is widely utilized by both U.S. and international government and law enforcement agencies to identify digital steganography applications on confiscated digital media. Additionally, there exist various steganalysis tools, available both for free and as paid options. For instance, StegSpy [Citation46,Citation48] is a free, portable signature analysis tool compatible with older Windows® machines (XP-). StegSpy can effectively identify messages concealed by steganography tools such as Hiderman, JPHideandSeek, Masker, JPegX, and Invisible Secrets.
3.1.2. Statistical-based
Statistical techniques are a category in image steganalysis that analyses the properties of the image by utilizing statistical methods like Chi-square analysis [Citation4,Citation15,Citation16,Citation43], Raw Quick Pair (RQP) [Citation4,Citation9,Citation43], RS steganalysis [Citation9,Citation10,Citation16,Citation43]. Most of the statistical techniques, including the aforementioned methods, have been applied in various currently used steganalysis tools, such as StegDetect and VSL – Virtual Steganography Laboratory. An important point that researchers have discovered in 2 papers [Citation4,Citation9], is that in case only the stego object is known, then statistical steganalysis outperforms the signature one in terms of effectiveness and robustness [Citation4,Citation9]. In the next paragraphs, more information will follow on the obtained results from the research done on 3 popular and utilized statistical steganalysis sub-techniques [Citation49]. Based on the popularity and information available in the literature, the chosen sub-techniques were Chi-square analysis, RS steganalysis, and Raw Quick Pair (RQP) [Citation4,Citation16,Citation50].
Starting with the Chi-square analysis, which concentrates on Pairs of Values (POVs) exchanged during the secret data embedding inside the digital image [Citation50]. The POVs could be pixel values, quantized DCT coefficients, or pallet indices, depending on the steganography algorithm used. It has been found that, if there is hidden information inside an image, then the embedded information alters the histogram of colour frequencies inside the image in a particular way. This constitutes a change in the least significant bits of the image, and the frequencies of POVs are prone to be situated further from the mean POV [Citation4,Citation16]. Overall, the chi-square analysis detects reliably messages that are sequentially embedded, however, doesn’t provide high accuracy for randomized ones [Citation4,Citation9].
RS steganalysis is another important technique, used to detect steganography inside images. It has been utilized for detecting the least significant bit (LSB) steganography in both colourful and grayscale images [Citation4,Citation9,Citation16,Citation50]. The RS analysis divides the image into groups and measures the noise within each group [Citation4]. The groups could be classified as either ‘regular’ or ‘singular’, depending on the results obtained after the LSBs of fixed pixels in the groups have been flipped and analysed whether the noise within the corresponding groups has increased or decreased [Citation9,Citation43]. Regarding the effectiveness of RS steganalysis, most of the examined papers during the literature review have concluded that it is more reliable in detecting steganography compared to the Chi-square method [Citation4,Citation9], however in case the embedded message inside the image is less than 0.005 bits per pixel, it is undetectable by RS steganalysis [Citation9]. Raw Quick Pair (RQP) is a statistical steganalysis technique, that detects steganography in 24-bit colour images by analysing close colour pairs that only differ in their LSB [Citation43]. The method has been shown to work well, especially in case the number of unique colours in the cover image is less than 30% of the number of pixels [Citation9]. The most notable disadvantage of RQP is the compatibility to work with only 24-bit colourful images and not with grayscale ones [Citation4,Citation9].
After examining the above-mentioned statistical sub-techniques and the statistical techniques in general, several important points could be emphasized. First, it has been suggested by certain researchers [Citation4,Citation9] that statistical methods are more accurate in detecting steganography, compared to the signature ones, in case only the stego object is accessible [Citation9]. For the detection accuracy, similarly to the signature-based techniques, in the examined literature no concrete information related to the accuracy of the sub-techniques was found. The following summarizes the above findings.
Table 2. Statistical sub-techniques overview.
3.1.3. AI-based
AI-based techniques are a set of methods used in steganalysis that aim to detect steganography in images, by using different types of AI algorithms and approaches, including machine learning (ME) and deep learning (DL) [Citation51]. Generally, the AI approaches in image steganalysis involve 2 steps. Initially to extract interesting and valuable features (could be size, colour, entropy, histogram) from the stego object, which is then compared with the cover image. Afterwards, the detection mechanism is built upon the examined data from the first step [Citation43,Citation51]. As discussed in the previous sections, steganalysis has different domains of techniques for detecting steganography. Signatures and statistical are one of the most popular ones. However, in most cases, these techniques require information regarding the steganography algorithm used for embedding the secret message inside the image [Citation4,Citation10]. An alternative category of techniques that do not utilize any additional information for the embedding algorithm is known as universal or blind steganalysis [Citation4,Citation10]. These techniques are in most cases implemented together with AI-based approaches. In the next paragraphs, the information obtained regarding 3 popular and widely referenced blind/universal steganalysis techniques is discussed and analysed.
A paper by Zhang et al. [Citation52], proposed a universal steganalysis algorithm, based on sparse representation, connected to finding steganography in JPEG images. The algorithm concentrates on transporting the main body of information with the minimum possible amount of information, in order to solve the information processing [Citation4,Citation32,Citation52]. This method has proven in experimental results to overcome several shortages which are common for SVM-based classifiers, like achieving high detection accuracy (around 90% [Citation32,Citation52] compared to SVM) and solving the over-fitting problem. of traditional classifiers. Furthermore, the algorithm used by Zhang et al. was demonstrated to be more effective when the image that needs to be detected has a Gaussian or Salt Pepper noise [Citation4,Citation32,Citation52]. Nevertheless, the most noticeable disadvantage of the algorithm is the limitation to perform the steganalysis on only JPEG images.
In 2012, a paper authored by Zong et al., A paper by Zong et al., proposed in 2012 for blind steganalysis in JPEG images. It concentrates on the correlation of inter- and intra-wavelet sub-bands in the wavelet domain and feature extraction from the co-occurrence matrix [Citation32,Citation53]. The algorithm depicts high-detection capabilities for several popular steganography tools (F5 [Citation29], Jsteg, Outguess [Citation38]) with around 95% detection accuracy and good detection capability for double-compressed images [Citation4,Citation32,Citation53]. Similarly, to the method utilized by Zhang et al., the solution is limited to the JPEG domain only.
In a paper authored by Desai et al., a universal image steganalysis method utilizing Fisher Criterion and ANOVA techniques was introduced. This approach involves the extraction of features from wavelet subbands and binary similarity patterns obtained from the DCT domain [Citation4,Citation43,Citation54]. The proposed method demonstrates more than promising results with an overall accuracy of 97%, obtained, against steganography algorithms such as Outguess [Citation38] and F5 [Citation29,Citation54]. The following summarizes the findings of the AI-based techniques.
Table 3. AI-based sub-techniques overview.
To conclude the AI techniques section, numerous papers were examined, mainly from the universal/blind steganalysis techniques domain. Overall, it was found that, currently, there does not exist a complete solution that has a high detecting rate independent of the steganography algorithm and image type used [Citation4,Citation32]. The sub-techniques that were examined, namely by Zhang et al., Zong et al., and Desai et al. demonstrated excellent results, against famous steganalysis algorithms such as F5 [Citation29] and Outguess [Citation38]. However, from the literature review, it was found that no universal/blind technique exists that could detect steganography in any image with high accuracy and low computational needs [Citation4,Citation43].
3.1.4. Image steganography and imagae steganalysis tools
In this section, we delve into both free and paid versions of the available image steganography and steganalysis tools applicable for Digital Forensic Investigation (DFI). The analysis focuses on evaluating stego image quality for JPEG images using metrics such as PSNR, MSE, color, and image capacity. The overview of each tool can be seen in .
Table 4. Image steganography tools.
3.1.4.1. Image steganography tools
Hide and Seek, as described by Wayner in 2002 [Citation46], represents one of the traditional Steganography techniques. This method employs a common approach and is relatively straightforward to implement in image files, as indicated by Johnson and Katzenbeisser in 2000 [Citation55]. The tool is available for free download. However, this is applicable to 8-bit color or 8-bit black and white GIF files with dimensions of 320 by 480 pixels, conforming to the standard size of the oldest GIF format [Citation46].
S-Tools (V. 4) is authored by Andy Brown [Citation46]. This package is capable of handling image or sound files through a unified program, S-TOOLS.EXE. In the case of a 24-bit image, such as a 24-bit BMP file [Citation55], S-Tools operates by modifying the least significant bit in each of the three colors within a pixel [Citation46]. However, the drawback with 24-bit images lies in their infrequent use on the web, making them easily noticeable compared to more common formats like GIF, JPEG, and PNG. This characteristic proves to be counterproductive for Steganography purposes. This is also a paid version.
Xiao Steganography [Citation56] is a freely available software designed for concealing confidential files within BMP images or WAV files. It offers encryption functionalities with a choice of algorithms, including RC4, Triple DES, DES, Triple DES 112, RC2, and hashing options such as SHA, MD4, MD2, and MD5. However, this software is not suitable for JPEG images.
F5 [Citation29] stands out as a widely used algorithm for concealing information within JPEG images. Notably, chi-square attacks prove ineffective against F5.
Outguess[Citation38] is another popular steganographic algorithm for concealing data within the most redundant content data bits of pre-existing (media) files. It supports image files in common formats like Netpbm and JPEG, allowing specific alterations to, for instance, the frequency coefficients of JPEG files. Developed in C, OutGuess is released as Free Software under the terms of the old BSD license.The chi-square attacks are not effective for OutGuess.
Steghide[Citation27] is open-source steganography software designed to conceal confidential files within image or audio files seamlessly. While there are no discernible changes to the image or audio file, your secret file becomes embedded within the original content.
Crypture[Citation57], a command-line tool specializing in steganography, enables the concealment of sensitive data within BMP image files. Thus, it is not suitable for JPEG images.
SteganographX Plus [Citation58] is a compact tool designed for concealing confidential data within BMP images, making it unsuitable for use with JPEG images.
Binwalk[Citation59,Citation60] is a program designed to scan binary images for embedded files and executable code, with a specific focus on identifying such elements within firmware packages. However, it is not applicable for use with JPEG images.
Invisible Secrets [Citation61] is an innovative software for steganography and file encryption. It enables the encryption of file and folder structures containing confidential data. Additionally, it provides the capability to conceal files, rendering them entirely invisible to any user. Nevertheless, this tool is not accessible for free.
Steganos Privacy Suite [Citation62] can be used to encrypt and hide files. This tool has a paid version available.
3.1.4.2. Image steganalysis tools
In this section, we examine both free and premium editions of image steganalysis tools. provides an overview of all the investigated image steganalysis tools, with highlighted entries in the table serving to justify the selection of specific tools for this research.
Aletheia [Citation30] is an open-source image steganalysis tool designed to identify concealed messages within images. Employing state-of-the-art machine learning techniques, Aletheia excels in detecting various steganographic methods, including F5 and Steghide.
StegExpose [Citation31] is a simple command line utility designed for detecting steganography in images. As a cross-platform tool, it provides a straightforward means to identify hidden messages within all the images within a specified directory.
StegoHunt [Citation63] represents the evolution of WetStone’s renowned steganography program detection tool and steganalysis suite. This advanced tool proficiently identifies the existence of steganography and data hiding programs, along with the potential carrier files where data payloads may be concealed. Accessible through a paid version.
Win Hex [Citation64] at its core is a versatile hexadecimal editor, specifically valuable in the domains of computer forensics and data recovery. A paid version of the tool is available.
AxiomCyber [Citation65,Citation66] is employed to scrutinize digital evidence gathered from mobile, cloud, computer, and vehicle sources, consolidating third-party extractions into a single case file. The tool offers a paid version.
Table 5. Image steganalysis tools.
3.1.5. Main observations
In the previous subsections, the results obtained from the Phase 1 regarding signature, statistical and AI-based techniques, their advantages, and disadvantages were discussed. The following flowchart depicts the most important observations and could serve as a road map for interested parties. Overall, it was examined that, currently, no best technique exists in the steganalysis domain that could detect steganography independent of the algorithm and image type used. In terms of the literature review, no details regarding the detection accuracy were demonstrated for the signature and statistical techniques. Contrarily, information on detection accuracy regarding AI-based was present in the literature. Despite the lack of concrete numbers for the detection accuracy in statistical-based and signature-based techniques, several recommendations could be followed.
Figure 1. Steganalysis technique selection.
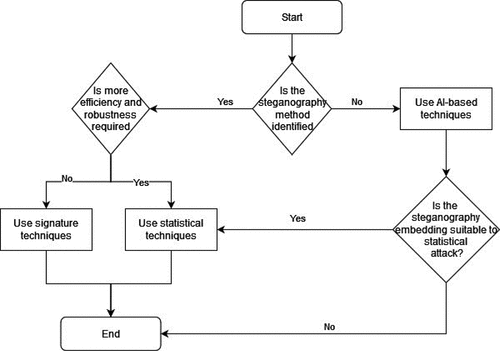
DFI and other specialists should prefer specific algorithms from the statistical domain when information is present regarding the steganography tool, utilized for embedding the message. Furthermore, forensic investigators should generally refrain from using signature techniques since the statistical ones are more accurate. Regarding AI-based techniques, such should be used when specific information is not available. However, these methods do not guarantee high detection in all cases. Finally, from the examined sub-techniques, it cannot be stated that, overall, AI-based techniques are more accurate than signature or statistics ones in detecting steganography.
Furthermore, we assess the current image steganography and steganalysis tools to determine the most effective ones for analyzing the JPEG image dataset among the freely accessible options. present a summary of these tools. Based on the aforementioned examination, we ultimately selected three image steganography tools, namely Outguess, StegHide, and F5 (highlighted in ), and two image steganalysis tools, Aletheia, and StegExpose (highlighted in ).
3.2. Tools comparison
In the tool comparison part, the methodology steps outlined earlier were followed. A sample of the JPEG image dataset of 512× 512 image size is showcased in .
Of all the 30 images, 16 images were used as cover images. Each cover image was then used to generate 5 different stego images, resulting from the embedding of 5 distinct hidden messages (m1 to m5). presents examples of these messages, where for m4 and m5, the” … ” signifies that more text is present after the three dots.
Table 6. Secret messages.
illustrates an example set of the cover images along with their corresponding stego images, classified by the embedded message size (m1 to m5) and the steganography tool (F5, Outguess, Steghide) employed. Regarding the experiment, in the following subsections, information regarding the detection capabilities of both steganalysis tools is discussed. It would be used to identify which of the tools is more accurate in detecting steganography. To simulate the role of the DFI and produce valuable insights, both Aletheia and StegExpose were utilized without prior knowledge of the embedded algorithm used.
Table 7. Cover and stego images.
3.2.1. StegExpose
Starting with StegExpose [Citation30], the tool achieved, overall, 50% accuracy, independent of the steganography tools used, or embedded message length, as evident from . From the conducted experiment, StegExpose was depicted to have correctly identified all images without embedded messages as non-steganographic. However, for the actual steganographic images, both grayscale and colourful, all the images were labeled as non-steganographic, which corresponds to a 50% false negative rate () and unreliability of the tool to detect steganography. Additionally, we assess Precision and Recall using the formulas (
) both of which align with a 50% value, which indicates the tool is making accurate positive predictions for only half of the cases, and missing the other half. In contrast, StegExpose achieves 100% accuracy on the test dataset provided by the developer, which consists of cover and stego images in the PNG format. Therefore, from the experimentation process, solely based on the utilized dataset and the provided PNG test dataset, it could be stated that StegExpose shouldn’t be utilized by DFI for detecting steganography. Nevertheless, it could produce reliable results in the PNG domain.
Table 8. StegExpose detection rate.
3.2.2. Aletheia
Aletheia is a novel steganalysis tool with multiple possible options, such as performing calibration, RS, and other attacks [Citation67]. However, for the scope of the current research, the default exploratory ‘auto’ detection functionality was utilized. It has built-in detection against 4 common steganography tools, namely Outguess, nsF5, Steghide, and J-UNIWARD [Citation40]. As it is evident, 3 of the common steganography tools corresponded to what was used for concealing the messages inside the JPEG images. Nevertheless, all the probability results were utilized for computing the detection accuracy, by taking the average of all probabilities. Such an approach was- chosen to be utilized since a DFI is in most cases not aware of the steganography algorithm used to embed a secret message inside an image [Citation68]. The following formula depicts the calculation of the accuracy:
If , the image is identified as stego
, the image is labelled as non-stego.
The experiment with Aletheia demonstrated that the tool obtained different results, depending on the steganography tool used for embedding the secret message, as showcased in .
Table 9. Aletheia detection rate.
For the first 3 sizes of hidden messages with lengths 6B, 53B, and 125B, the results per tool are identical, independent of the colour of the image (RGB or GS), achieving the highest accuracy against F5 and lowest against Outguess. Regarding the larger secret message length size of 529B and 1040B, Aletheia has the highest detection rate against F5 and the lowest against Steghide. Moreover, given the results, several aspects could be observed. Aletheia performed worse in detecting secret messages in grayscale images, embedded with Outguess, compared to the RGB ones. On the other hand, in F5 and Steghide, in both cases, the detection accuracy in grayscale images is bigger or equal to the colourful ones. Furthermore, it is evident that after surpassing the 512 secret message size thresholds, the detection accuracy in most cases is improved. This would indicate that the bigger the hidden message is, the higher the detection rate Aletheia could achieve.
3.2.3. Main observations
In summary, from the utilized popular steganography and steganalysis tools on the JPEG dataset, it has been observed that both steganalysis, Aletheia, and StegExpose tools, are still unreliable. With StegExpose, provided 50% false negative rates with 50% precision, which raised the question, of whether such a tool could be useful in any circumstances. On the other hand, Aletheia, depicted different results and findings, however with an average accuracy of 37.96% against Outguess, Steghide, and F5, which could puzzle researchers whether they should trust it. Therefore, despite having a higher average accuracy compared to Aletheia, StegExpose demonstrates a lower reliability, given the high false negative rate. Following that, several recommendations could be shared with DFI.
First and foremost, StegExpose should be avoided as the choice of steganalysis tool, based on the observed unreliability and more attention should be dedicated to Aletheia.
Given the default functionality of the latter one, which provides information regarding the possibility of a specific steganography tool that has been used, it could be used in an exploratory phase in detecting steganography in JPEG image files.
Subsequently, in case the steganography algorithm is F5 or Steghide, a concrete set of steps could be utilized by DFI, such as DL models and calibration attacks that perform well in detecting steganography, against the aforementioned tools [Citation67].
3.3. Image features analysis
Regarding image features analysis, the same dataset from RQ2 was utilized, however, consisting solely of stego images. The metrics evaluation was performed on the images, to detect whether values such as peak signal-to-noise ratio (PSNR), mean square error (MSE), colour, and size indicate if an image is stego, or are totally independent in that respect. The results were analysed and divided into separate subsections based on the steganography tool that was utilized. Only a sample of 6 images, 3 colourful (BC, CC, SC) and their respective grayscale (BG, CG, SG) were analysed. In , the ‘Average Stego Image Size in Bytes’ column, indicates the average value that was obtained, given the sizes of stego images with 6B, 53B, 125B, 529B, and 1040B embedded secret messages.
Table 10. Sample stego images values.
In reference to two of the selected features, PSNR and MSE, several assumptions were taken into consideration. Based on the definition of MSE (please refer to Section 2), the closer a value is to 0, the closer the stego image is to the cover one. Regarding PSNR, following the formula, since MSE appears in the denominator of the logarithm base 10 part, it can be concluded, that the bigger the PSNR is, the better quality the stego image has. Therefore, to analyse the results more systematically, statistical techniques such as mean values and standard deviation were computed. They should serve to check whether the embedded message size significantly alters the stego image size. In the following subsections, the research results are analysed, based on the steganography tool.
3.3.1. F5
From the chosen sample of 6 images, several interesting observations were found in . The grayscale stego (GS) images have a smaller size in terms of Bytes compared to the respective colourful ones. However, such a detail may be viewed as expected, since the former one has one channel with 8 bits, whereas the latter one has three channels with 8 bits each.
Table 11. F5 stego images feature analysis results.
Another observation related to the size was the increase in the hidden messages’ lengths, correlating to the respective decrease in the stego image sizes. Regarding the MSE, from the chosen sample of 6 images, it was demonstrated that the MSE value increased with the increase of the embedded message size. Furthermore, especially for the RGB images, the mean MSE value is higher than the respective GS images, indicating that the RGB stego image quality is compromised and worse, compared to GS. Similar trends are observable in the case of PSNR, with GS stego images consistently exhibiting superior quality. Also, the similar trend can be observed for root mean square error (RMSE). The grey scale images are having lesser RMSE values in comparison to RGB images which indicates relatively small errors compared to the RGB images.
3.3.2. Outguess
Compared to F5 [Citation29], Outguess [Citation38], delivered different values for some examined features as presented in . The sizes of the stego images were still smaller than the respective cover images, however, compared to F5, with the increase of the embedded message size, the stego size also increased. Moreover, compared to F5, the stego sizes with different secret messages were closer in terms of size than the respective ones in F5. As a result, the standard deviation of the aforementioned feature was approximately 2 times smaller, compared to F5, illustrating that Outguess hides the messages more efficiently. In terms of MSE and PSNR, the dataset from Outguess the values are higher and lower, compared to F5, indicating that F5 delivers better quality for the stego images. Furthermore, a comparison of RMSE values between F5 and Outguess reveals that F5 demonstrates lower errors for both greyscale and RGB images. This observation reinforces the preference for F5 over OutGuess as a steganography tool.
Table 12. Outguess stego images feature analysis results.
3.3.3. Steghide
Steghide [Citation27], showed the most interesting results, compared to F5 and Outguess in . In contrast to F5 and Outguess’s stego images, Steghide had a bigger image size in terms of Bytes for the grayscale stego images than the colourful ones.
Table 13. Steghide images feature analysis results.
Furthermore, the average Bytes size of all stego images was the highest, compared to their respective counterparts in F5 and Outguess, indicating that Steghide doesn’t perform efficiently with grayscale images. However, the standard deviation of the stego image sizes with different embedded messages was observed to be the lowest, depicting that the size of the stego image wasn’t influenced significantly by the increase of the concealed message size. The MSE and PSNR values, were the lowest and highest, respectively, from all examined tools, indicating that the image quality has been the best. The similar analogy can be seen from the table for RMSE as well.
3.3.4. Main observations
From the experimentation process, regarding the image features analysis, several conclusions could be drawn.
Each of the utilized steganography tools affected differently the dataset of images. For instance, Steghide produced larger sizes for grayscale stego images, compared to F5 and Outguess, whereas F5 had the highest value for the standard deviation of the stego image sizes, indicating the inefficient embedding of secret messages inside the cover images. In terms of the MSE and PSNR values, no general information was found, that would indicate an image being stego.
From the conducted experiment, Outguess demonstrated the highest and lowest average values for MSE and PSNR, in contrast, Steghide depicted the lowest and highest, from all the 3 steganography tools, respectively, which substantiate Steghide as a superior tool compared to OutGuess and F5.
Finally, based on the conducted experiment, it can be stated that none of the tested features (PSNR, MSE, colour, and size), directly indicate the existence of a hidden message inside an image. Following that, DFI cannot rely on any of the tested features. This is, because none of the 3 examined steganography tools, provoked similar or predictable changes in the tested features. Therefore, PSNR, MSE, colour, and image size should not be used as markers to discover steganography in JPEG images.
4. Conclusion & future work
The current study focused on different aspects of the domain of steganography and steganalysis. The general aim of the research was to aid DFI in tackling challenges in the field of image steganography and steganalysis. The results showed that AI-based blind/universal steganalysis techniques are not better than statistical or signature-based. Nevertheless, blind/universal techniques should be used when the utilized steganography algorithm is unknown. On the other hand, statistical and signature-based should be utilized when the concrete steganographic algorithm is known. Regarding the steganalysis tool comparison, Aletheia was identified as more reliable, despite achieving lower accuracy than StegExpose. After conducting experiments, we also analyzed the steganography tool Steghide is more reliable in comparison to OutGuess, and F5. Finally, for the study of the metrics, no concrete information was found that identified the size, colour, MSE, or PSNR as an indication of the existence of a hidden message inside a JPEG image.
For future work, several new directions can be followed. For example, more emphasis could be focused on experimenting with different image formats (PNG, GIF). Furthermore, some paid, contemporary steganography and steganalysis tools, could be studied and compared, on a dataset consisting of images with different dimensions. From such newly followed approaches, more insightful conclusions could be made, regarding the image steganography and steganalysis domain.
Disclosure statement
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Notes on contributors
Kristian D. Michaylov
Kristian D. Michaylov holds a bachelor’s degree in computer science. Currently, he is pursuing his master’s degree in computer science with a specialization in Cyber Security. His main interests are the Steganography and Cryptography.
Dipti K. Sarmah
Dipti K. Sarmah works in the group Semantics, Cybersecurity & Services (SCS) at the University of Twente. Her research interests are not only limited to the field of steganography, and cryptography, and its applications but also the study and analysis of human behaviour for Cyber security. Her latest research has been accepted in the Journal of Computers & Security, Elsevier. In addition, she has published her research work (to name a few) in the Journal of Information Security and Applications, Information Sciences, Journal of Cyber Security Technology, and Taylor & Francis. She is also the author of a book published in the Intelligent Systems Reference Library, Springer.
References
- Kahn D. The history of steganography. In: Anderson R, editor. Information hiding. Lecture notes in computer science. Berlin, Heidelberg: Springer, 1996. p. 1–5. https://link.springer.com/content/pdf/10.1007/10719724.pdf.
- Cheddad A, Condell J, Curran K, et al. Digital image steganography: survey and analysis of current methods. Signal Process. 2010;90(3):727–752. doi: 10.1016/j.sigpro.2009.08.010
- Poisel R, Tjoa S. 2011. Forensics Investigations of Multimedia Data: a review of the state-of-the-art. In: 2011 Sixth International Conference on IT Security Incident Management And IT Forensics, p. 48–61. 10.1109/IMF.2011.14.
- Karampidis K, Kavallieratou E, Papadourakis G. A review of the image steganalysis techniques for digital forensics. J Inf Secur Appl. 2018;40(2018):217–235. doi: 10.1016/j.jisa.2018.04.005
- Cameron L. With cryptography easier to detect, cybercriminals Now hide malware in plain sight. Call it steganography. Here’s How It Works. [cited 2023 Oct 10]. https://www.computer.org/publications/tech-news/research/how-steganography-works.
- Olzak T. 2019. The security challenges and defense of hidden data. [cited 2023 Oct 10]. https://www.spiceworks.com/it-security/data-security/articles/the-security-challenges and-defense-of-hidden-data/
- Provos N, Honeyman P. Hide and seek: an introduction to steganography. IEEE Secur Privacy. 2003 May-June;1(3):32–44. doi: 10.1109/MSECP.2003.1203220
- How to Become a Digital Forensic Investigator. 2023 [cited 2023 Oct 10]. https://www.wgu.edu/career-guide/information-technology/digital-forensic-investigator-career.html
- Nissar A, Mir AH. Classification of steganalysis techniques: a study. Digital Signal Process. 2010;20(6):1758–1770. doi: 10.1016/j.dsp.2010.02.003
- Farooq N, Selwal A. Image steganalysis using deep learning: a systematic review and open research challenges. J Ambient Intell Human Comput. 2023;14(6):7761–7793. doi: https://doi.org/10.1007/s12652-023-04591-z
- Sajedi H. Steganalysis based on steganography pattern discovery. J Inf Secur Appl. 2016;3030:3–14. doi: https://doi.org/10.1016/j.jisa.2016.04.001
- YangzlTHU: IStego100K. original-date: 2019-07-10T03:03:05Z. 2023. [cited 2023 Oct 10]. https://github.com/YangzlTHU/IStego100K
- Bas P, Filler T, Pevny T. Break our steganographic system: the Ins and outs of organizing BOSS. In LNCS, information hiding. Vol. 6958, Berlin, Heidelberg: Springer. p. 59–70. doi: 10.1007/978-3-642-24178-9_5
- Mstafa R, Bach C. 2013. Information hiding in images using steganography techniques. ASEE Northeast Section Conference; 2023 Oct 10; Norwich University. 10.13140/RG.2.1.1350.9360
- Rustad S, Andono PN, Shidik GF. Digital image steganography survey and investigation (goal, assessment, method, development, and dataset. Signal Process. 2022;206:108908.
- Bachrach M, Shih FY. Image steganography and steganalysis. Wiley Interdiscip Rev Comput Stat. 2011;3(3):251–259. doi: 10.1002/wics.152
- Chutani S, Goyal A. A review of forensic approaches to digital image Steganalysis. Multimedia Tools Appl. 2019;78(13):18169–18204. doi: 10.1007/s11042-019-7217-0
- Mandal PC, Mukherjee I, Goutam P, et al. Digital image steganography: A literature survey. Inf Sci. 2022;609:1451–1488. ISSN 0020-0255. doi: 10.1016/j.ins.2022.07.120
- Sharma A, Batta A, Sharma VK. 2021 Fifth international conference on I-SMAC (IoT in social, Mobile, Analytics and cloud) (I-SMAC) palladam, India 2021 Nov. 11 - 2021 Nov. 13. (2021). 2021 fifth international conference on i-smac (iot in social, mobile, analytics and cloud) (i-smac). In A review on image steganography and its applications; India. (pp. 1466–1473). Essay, IEEE.
- Giarimpampa D. 2018. Blind image steganalytic optimization by using machine learning. [cited 2023 Oct 10]. https://urn.kb.se/resolve?urn=urn:nbn:se:hh:diva-38150
- Johnson NF, Jajodia S. Steganalysis of images created using Current steganography software. In: Aucsmith D, editor. Information hiding. IH 1998. Lecture notes in computer science. Vol. 1525. Berlin, Heidelberg: Springer; 1998. doi: 10.1007/3-540-49380-8_19.
- Ruan F, Zhang X, Zhu D, et al. Deep learning for real-time image steganalysis: a survey. J Real Time Image Proc. 2020;17(1):149–160. doi: https://doi.org/10.1007/s11554-019-00915-5
- Arivazhagan S, Amrutha E, Sylvia LJW, et al. Digital image steganalysis: a survey on paradigm shift from machine learning to deep learning based techniques. IET Image Process. 2021;15(2):504–522. doi: 10.1049/ipr2.12043
- Lin L. The impact of exposure settings in digital image forensics. 2018 25th IEEE International Conference on Image Processing (ICIP), Athens, Greece, 2018, pp. 540–544, doi: 10.1109/ICIP.2018.8451688.
- Sarmah DK, Kulkarni AJ. Improved Cohort Intelligence—A high capacity, swift and secure approach on JPEG image steganography. J Inf Secur Appl. 2019;45:90–106. doi: 10.1016/j.jisa.2019.01.002
- Black Hat: Advanced JPEG Steganography and Detection by John Ortiz. 2014 [cited 2023 Oct 10]. https://www.youtube.com/watch?v=BQPkRlbVFEs
- Steganalysis, High Capacity Despite Better, and Andreas Westfeld. F5—A steganographic algorithm. Information Hiding: 4th International Workshop, IH 2001, Pittsburgh, PA, USA, April 25-27, 2001. Proceedings. Vol. 2137. Springer, 2001.
- Steghide. 2023, Nov 10. https://sourceforge.net/projects/steghide/
- Provos N. 2002. Outguess. Software. www.outguess.org.
- Lerch-Hostalot D. Aletheia. 2021. doi: 10.5281/zenodo.4655945
- snoop: StegExpose. 2023 original-date: 2014-08-03T08:38:52Z. [cited 2023 Oct 10]. https://github.com/b3dk7/StegExpose
- Butora J, Puteaux P, Bas P. 2022. Errorless Robust JPEG Steganography using outputs of JPEG coders. [cited 2023 Oct 10]. https://arxiv.org/abs/2211.04750.
- Badr M, Salama SI, Selim GI, et al. A review on steganalysis techniques: from image format point of view. Int J Comput Appl. 2014;102(4):11–19. doi: 10.5120/17802-8617
- Unsplash: Beautiful Free Images & Pictures | Unsplash. 2023 [cited 2023 Oct 10]. https://unsplash.com/
- Forensic-Investigation: Steganography and Steganalysis for Enhanced Forensic Analysis and Recommendations. 2023. original-date: 2023-07-26T11:43:37Z. [cited 2023 Oct 10]. https://github.com/Forensic-Investigation/
- Make grayscale image online - Free tool. 2023 [cited 2023 May 29]. https://grayscale.imageonline.co/
- iLovePDF: Resize multiple images at once!. 2023 [cited 2023 Oct 10]. https://www.iloveimg.com/resize-image.
- Provos N. Defending against statistical steganalysis. 10th USENIX Security Symposium (USENIX Security 01); Washington, D.C. 2001.
- Usage Statistics of Image File Formats for Websites. 2023 June. [cited 2023 Oct 10]. https://w3techs.com/technologies/overview/image_format
- Dalal M, Juneja M. Steganography and Steganalysis (in digital forensics): a cybersecurity guide. Multimedia Tools Appl. 2021;80(4):5723–5771. doi: 10.1007/s11042-020-09929-9
- Luck A. 2023. stegdetect. original-date: 2013-04-09T09:32:34Z. [cited 2023 Oct 10]. https://github.com/abeluck/stegdetect
- Samajdar T, Quraishi MI. Analysis and evaluation of image quality metrics. In: editors, Mandal J, Satapathy S, Kumar Sanyal M, Sarkar P, and Mukhopadhyay A. Information systems design and intelligent applications. Advances in intelligent systems and computing. Vol. 340. New Delhi: Springer; 2015. p. 369–378.
- Eid WM, Alotaibi SS, Alqahtani HM, et al. Digital Image Steganalysis: Current Methodologies and Future Challenges. IEEE Access. 2022;10:92321–92336. doi: https://doi.org/10.1109/ACCESS.2022.3202905
- Karampidis K. Image Steganalysis for Digital Forensics [ PhD thesis]. University of the Aegean, (2020). https://icsdweb.aegean.gr/aegeanrbtcs/wpcontent/uploads/2021/11/Karampidis_PhD_Dissertation.pdf
- Hammad BT, Ahmed IT, Jamil N. A steganalysis classification algorithm based on distinctive texture features. Symmetry. 2022;14(2):236. doi: 10.3390/sym14020236
- Hassan NA, Hijazi R. Chapter 6 - data hiding forensics. In: Hassan NA Hijazi R, editors.Data hiding techniques in Windows OS. Syngress. 2017. p. 207–265. ISBN 9780128044490. doi: 10.1016/B978-0-12-804449-0.00006-3
- Joshi I, Utkarsh A, Kothari R, et al. On estimating uncertainty of fingerprint enhancement models. In: Nafis UK, Amit KS, Karm VA, editors. Digital Image Enhancement and Reconstruction. Academic Press; 2023. p. 29–70. https://doi.org/10.1016/C2021-0-01039-7
- Hasan M. Stego analysis with StegSpy. LinkedIn; 2017. https://www.linkedin.com/pulse/stego-analysis-stegspy-mehedi-hasan/
- Fridrich J, Goljan M, Du R. Steganalysis based on JPEG compatibility. In: Multimedia systems and applications IV. Vol. 4518. SPIE; 2001. p. 275–280. https://doi.org/10.1117/12.448213.
- Hassan M, Amin M, Mahdi S. Steganalysis techniques and comparison of available softwares. In:Raed AA, Rana Z, Obed A, editors. Proceedings of the 1st International Multi Disciplinary Conference Theme: Sustainable Development and Smart Planning, IMDC SDSP 2020, Cyperspace, 28-30 June 2020. EAI, Cyberspace. https://eudl.eu/proceedings/IMDC-SDSP/2020
- Hussain M, Wahab AWA, Idris YIB, et al. Image steganography in spatial domain: a survey. Signal Process Image Commun. 2018;65:46–66. doi: 10.1016/j.image.2018.03.012
- Mehta P, Nair A, Edappilly S, et al. A comprehensive study of AI-Based steganalysis techniques on image and text documents. In: Tiwari S, Trivedi MC, Kolhe ML, Mishra KK Singh BK, editors. Advances in data and information sciences. Lecture notes in networks and systems. Springer; 2022. p. 53–63. doi: 10.1007/978-981-16-5689-7_5.
- Zhang Z, Hu D, Yang Y, et al. 2013. A universal digital image steganalysis method based on sparse representation. In: Ninth International Conference on Computational Intelligence and Security, p. 437–441. 10.1109/CIS.2013.99
- Zong H, Liu F-L, Luo X-Y. Blind image steganalysis based on wavelet coefficient correlation. Dig Inv. 2012;9(1):58–68. doi: 10.1016/j.diin.2012.02.003
- Wayner P. Disappearing cryptography. 2nd ed. USA: Morgan Kaufmann Publishers; 2002.
- Johnson NF, Katzenbeisser S. A survey of steganographic techniques. In: Katzenbeisser S, and Petitcolas FAP, editors Information hiding techniques for steganography and Digital Watermarking. Norwood: Artech House, INC; 2000. p. 43–78.
- Steganography X-C. 2020. Software. https://github.com/Xiao-Chong/steganography
- Crypture. 2021. Software. https://sourceforge.net/projects/crypture/
- SteganographX Plus. 2010. Software. https://leelusoft.blogspot.com/2010/03/steganographx-plus.html
- Roy AS. 2023. Analysing and extracting firmware using Binwalk. Medium. https://fr3ak-hacks.medium.com/analysing-and-extracting-firmware-using-binwalk982012281ff6#:~:text=What%20is%20Binwalk%20%3F%3F%3F,information%20security%20researcher%2C%20like%20yourself
- Binwalk. 2023. Software. https://github.com/ReFirmLabs/binwalk
- east-tec InvisibleSecrets. Software. https://www.east-tec.com/invisiblesecrets/
- Steganos Privacy Suite. Software. https://www.steganos.com/en/xmas-2023-steganos-privacy-suite
- StegoHunt™ MP. Steganalysis and Steganography Detection Tool. Software https://www.wetstonetech.com/products/stegohunt-steganography-detection/
- WinHex: Computer Forensics & Data Recovery Software, Hex Editor & Disk Editor. https://www.x-ways.net/winhex/
- Magnet Axiom. Recover & analyze your evidence in one case. Software https://www.magnetforensics.com/products/magnet-axiom/
- Desai MB, Patel SV, PrajapatI B. ANOVA and Fisher criterion based feature selection for lower dimensional universal image Steganalysis. Int J Image Process. 2016;10(3):145–160.
- Hostalot DL Introduction to steganalysis with Aletheia. [cited 2023 Oct 10]. https://daniellerch.me/stego/aletheia/intro-en/.


