?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
Image encryption is not new. Several different encryption algorithms have been used. Some of the algorithms are based on random sequences generated using chao systems and DNA sequencing and others are based on compression. Still, others are based on Linear Feedback Shift Registers. This paper focuses on research solutions for securing digital images including medical images. Medical images are important and are generally regarded as sensitive in nature. In this research paper, higher order linear feedback shift registers are developed using combination of lower order LFSRs by suitable clocking and the ciphers generated are utilized to encrypt digital images. Our analysis involves using suitable metrics to compare the chaos-based and LFSR-based stream ciphers for image encryption.
1. Introduction
Data remains a critical component in information technology. Whether data is in motion or at rest, preserving it during transmission or in storage remains one of several challenges facing the information technology industry and business organizations. Business organizations both in the private and public sectors want assurances regarding the security of all organization’s owned critical data assets. In addition to data assets relating to organization’s products and services, businesses keep pertinent records of customers and clients. Business organizations want to be entrusted with the privacy of personal identifiable information of all customers and clients. Malicious attacks on information systems for managing data assets continue to be of major concern to many organizations. Organizations are saddled with security attacks on data assets that have serious impacts on investments and profitability.
Typically, data that is being transmitted via unsecured media need to be encrypted before transmission to render the information contained in data obfuscated. When an adversary accesses the resultant encrypted data, the adversary will be unable to recover or learn any information from the encrypted data. As a matter of convention, the encryption algorithm is publicly available. However, the encryption algorithm uses keystream that is secret and known only to the sender and the receiver. The receiver of the data must be able to recover the original data using a corresponding algorithm called decryption. The encryption and decryption algorithms are collectively called a cipher. A cipher is either symmetric (that is, it uses a single key called secret key) or asymmetric (uses two keys with one being a secret key called private key and the other called a public key). In the case of asymmetric cipher or public key cipher, the private key is only known to the receiver and the public key is widely distributed and readily available to anyone who wants to send data (or message) to the receiver. The sender encrypts data with a public key before sending to the receiver, who uses the private key to decrypt the encrypted data.
This paper focuses on the use of symmetric ciphers, particularly stream ciphers, for the encryption of digital images. While there is a variety of stream ciphers, the chaos-based and the linear feedback shift registers-based ciphers have gained significant momentum in the recent past years [Citation1,Citation2]. Both ciphers generate keystreams that are assumed to have significant levels of randomness.
2. Chaos-based ciphers
The chaos-based ciphers use chaotic maps obtained from simulations of dynamical systems using suitably chosen system parameters, see [Citation3,Citation4,Citation5,Citation12]. The values of chosen systems parameters become the secret key for the cipher. For example, a logistic map defined as has
as the secret key. The keystream that is used for the cipher is generated from the simulation:
, where
Here, the generated values
are discarded. While this may not be necessary, it ensures an additional requirement for the secret key. For the paper, the following dynamical systems were used to generate chaotic maps:
Logistic:
Tent:
One-Dimensional Henon (Henon1D):
Two-Dimensional Henon (Henon2D):
Although, there are a lot more sophisticated chaotic maps such as those based on Lorenz Systems for image encryption, the simulations for these listed maps do not require complicated operations such as numerical solutions of differential equations. Since our images are in the portable network graphics (PNG) file format and the type of PNG image, we used in this paper has four (4) colors in each pixel representing red, green, blue, and alpha (or transparency) channels. Since each color is 8-bit, each is converted to the equivalent of 8-bit integer using the formula
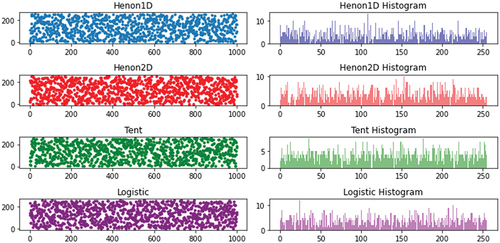
. The values generated from each map after 1,000 iterations with
are depicted in .
Figure 1. Pseudorandom noise sequences generated from chaotic maps.
3. Linear feedback shift registers and proposed ciphers
A linear feedback shift register (LFSR) is fundamentally based on a linear array of D-type flip flops, see [Citation6–10]. The flip flops are clocked to be in two stable states. As a finite state machine, flip flops have initial values which constitute the initial state of the LFSR. An LFSR of order n will have an initial state consisting of a sequence of bits, . Not all the flip-flops are clocked. A flip flop that is clocked has an output of 1 and the one that is not clocked has an output of 0. Generally, these values are called taps and they serve as connections for the input of the LFSR, i.e. they are used in calculating the input for the LFSR, hence the feedback mechanism. The output of an LFSR is usually the most significant bit of the LFSR bit sequence. Sequence states of the LFSR are obtained through a left or right shift of memory bit of one flip flop to the next. The way the input values are calculated for the LFSR is what gave rise to the two popular approaches, namely the Fibonacci and the Galois LFSR [Citation8,Citation9]. Let denote the values of the tap flip flops by the connection vector
, the Fibonacci LFSR is defined by the following recurrence formula:
In this case, the output of each flip flop contributes externally only to the input of the least significant bit, hence it is called external LFSR. The Galois LFSR is represented by
The output contributes internally to the inputs of each flip flop; hence, it is called internal LFSR. While the two approaches will generate a pseudorandom noise (PN) sequence (not necessarily equal) starting with the same initial state vector, however, they will result in the same state vectors after ( clock cycles without counting the zero-state vector. For example, if
the number of possible state vectors is 7 not counting the zero state vector:
An LFSR is defined by its connection vector and the simulated LFSR will visit some if not all of these state vectors. A simulated LFSR that visits all the possible state vectors is called a maximum period LFSR. Maximum period LFSRs are used in this paper.
The output sequence using a single Fibonacci-based LFSR is
where,
The way to obtain the d-bit sequence is to discard the first several bits of the output bit sequence and subsequently picking the next d consecutive bits. Let us define the d-bit sequence as
and the bit pattern representation of an image (pixel) as
The encrypted image (pixel) is obtained using XOR, thus,
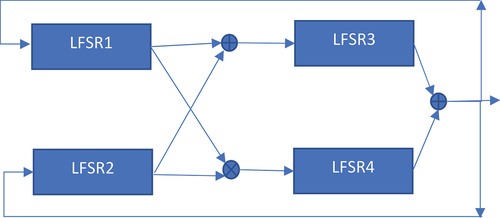
To decrypt the encrypted image, we would use: It is a common practice to combine LFSRs in a nonlinear fashion. Our proposed cipher combines four LFSRs of the same degree (we call it Simple Combined LFSR). The output of the first two LFSRs will be ORed and XORed to form the input of the remaining two LFSRs as shown in . Although, we use LFSRs of the same order in this paper, it is, however, possible to use LFSRs of different orders; however, the algorithm must be modified so that the most significant registers of LFSR1 and LFSR2 are XORed with the corresponding
when the output bit is 1.
Figure 2. Proposed LFSR cipher.
The following LFSR ciphers are tested in this paper.
[SCLFSR5] Simple Combined LFSR Cipher with LFSRs defined as LFSR1(c = 37), LFSR2 (c = 41), LFSR3 (c = 47) and LFSR4 (c = 61) [SCLFSR5]. Each LFSR has a 5-bit state vector.
[A5/1] A5/1 Cipher with LFSRs defined as LFSR1 (c = 8388607), LFSR2 (c = 4194303), LFSR3 (c = 524287) with irregular clocking using registers 13 of LFSR1, 12 of LFSR2 and 11 of LFSR3. Just like SCLFSR5, the outputs from the three LFSRs are XORed for a 1-bit output. To have output like the original A5/1, we simulated 1000 times with regular clocking and another 1000 times with irregular clocking before generating the desired keystream.
[SCLFSR24] Simple Combined LFSR Cipher with LFSRs defined as LFSR1 (c = 16777243), LFSR2 (c = 28311553), LFSR3 (c = 16777351), and LFSR4 (c = 29491201). Each LFSR has a 24-bit state vector.
[LFSR24] A single LFSR (c = 29491291). This LFSR has a 24-bit state vector.
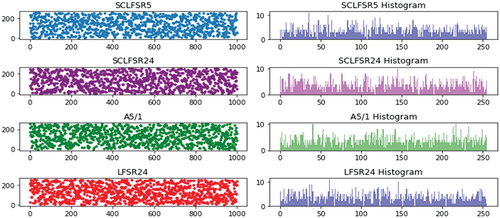
In a previous paper, the Python library for LFSRs and associated polynomials in Galois field were described [Citation11]. The library has two classes, namely, Gf2Poly representing polynomials in Galois field and the LFSR representing linear feedback shift registers. The Gf2Poly class has an integer attribute that is used to represent the polynomial and the LFSR class has two attributes, one integer attribute representing the current state of the LFSR, and the second attribute is a Gf2Poly object representing the taps, the c value(s) in the parenthesis. The period of each LFSR of order 5 (i.e. a 5-bit LFSR) used in the SCLFSR was calculated to be As demonstrated in , single 5-bit LFSR would not be suitable for image encryption. There is clearly a pattern in the 1,000 PN sequences of size 8-bit as appose to the chosen 24-bit LFSR with a period of
Figure 3. PN sequences and histogram profiles.
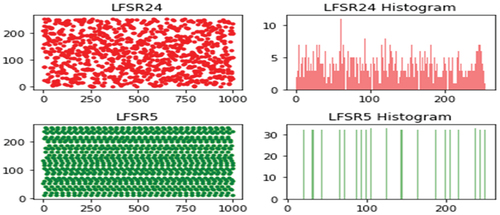
Like the chaotic maps, we computed the 1,000 PN sequences each of size 8-bit and presents the plots of the PN sequences and their histogram profiles.
4. Image encryption and analysis
As indicated previously, a digital image (png) consists of 4-value pixels arranged in M rows and N columns. In the case where a pixel has less than 4 values, the algorithm must be modified accordingly. The encryption is done in two steps once the pixel values of the image have been determined. In the first step, we generate PN-sequence of size 4N using the appropriate cipher and encrypt each image row with the generated PN-sequence. This is called row wise encryption. The second step involves generating a second PN-sequence of size 4 M and encrypting the encrypted image from the first step with the second generated PN-sequence. Denote the 4M by 4N pixel values by IMAGE(I,J) and the 4N PN-sequence by ROW(I) and the 4 M PN-sequence by COL(J), the encrypted image, denoted by CIMAGE(I,J) is obtained using:
The symbol ⊕ stands for exclusive OR operator. The PN sequences ROM(I) and COL(J) are generated using different initial parameters for both the chaos and linear feedback shift register ciphers. Note that the final state values of the simulation generating ROW(I) are used as the initial state values for the simulation generating COL(J).
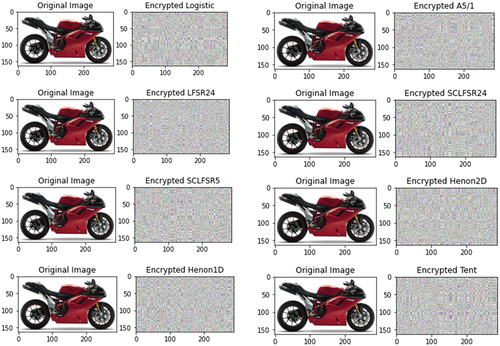
The encrypted images generated by all eight ciphers are shown in .
Figure 5. Encrypted images by LFSR-Based and chaotic maps ciphers.
The two popular metrics for measuring the security strength of image encryption algorithms are the unified average changing intensity (UACI) and number of pixels change rate (NPCR) which are defined as
Here, is the color value of pixel in the i-th row and j-th column of the original image and
is the color value of pixel in the i-th row and j-th column of the encrypted image. These two metrics measure the sensitivity of the encryption algorithm when there is a small change in the original image, see [Citation5,Citation12]. These numbers determine the difficulty of the encryption algorithms to differential attacks. The NPCR and UACI values for all tested ciphers as shown in are indications of their sensitivity to small changes in the pixel of the original image. The NPCR values for all algorithms are greater than 99% and UACI values are greater than 40%.
Table 1. Calculated NPCR and UACI Values.
5. Conclusions
In this paper, the chaos-based ciphers were compared with linear feedback shift registers-based ciphers. Except for the A5/1 ciphers, all LFSR-based ciphers are new and are still being developed. While the theoretical randomness properties are currently being studied and will be reported in a different paper, the histogram profiles of the keystream sequences generated from all ciphers show randomness at best. One cannot infer any meaningful information from the encrypted images and the computed NPCR and UACI further indicate the strength of the ciphers from differential attacks.
Acknowledgments
This paper is partly supported by the National Science Foundation through the Excellence in Research (EiR) Program, Award #CNS 23000239.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
References
- Momeni A, Broumandnia A, Mirabedini SJ. Color image encryption using linear feedback shift registers by three-dimensional permutation and substitution operations. Int J Nonlinear Anal Appl 2021;12: 903–921. Special Issue, Winter and Spring doi: 10.22075/IJMA.2021.5520
- Pan H, Lei Y, Jian C. Research on digital image encryption algorithm based on double logistic map. J Image Video Proc. 2018;142(1). doi: 10.1186/s13640-018-0386-3
- Allawi ST, Al-A’meri JH. Image encryption based on linear feedback shift register method. Al-Sadeq International Conference on Multidisciplinary in IT and Communication Science and Applications (AIC-MITCSA) – IRAQ; 2016. p. 9–10. https://ieeexplore.ieee.org/document/7759903
- Feng L, Du J, Fu C. Digital image encryption algorithm based on double chaotic map and lstm. Comput Mater Continua. 2023;77(2):1645–1662. doi: 10.32604/cmc.2023.042630
- Sankpal PR, Vijaya PA. Image encryption using chaotic maps: a survey. Procs of the 5th International Conf on Signal and Image Processing, ICSIP; 2014. p.102–107. https://ieeexplore.ieee.org/document/6754860
- Bhowmik A, Karforma S. Linear feedback shift registers and integer theory: a state-of-art approach in security issues over e-commerce. Electron Commer Res. 2021;22(4):1–21. doi: 10.1007/s10660-021-09477-w
- Hou S, Deng D, Wang Z, et al. A dynamically configurable LFSR-based PUF design against machine learning attacks. CCF Trans High Perform Comput. 2020;3(1):31–56. doi: 10.1007/s42514-020-00060-7
- Okunbor D. Software implementation of LSFR-based stream ciphers for GSM cryptosystems. IEEE Procs 7th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO); 2018. p. 59–65. doi: 10.1109/ICRITO.2018.8748397
- Sachs J. Linear feedback dhift registers for the uninitiated parts I-XVIII. 2017. https://www.embeddedrelated.com/showarticle/1193.php
- Sadkhan SB, Jawad NH. Simulink based implementation of developed A5/1 stream cipher cryptosystem. Procedia Computer Science. 2015;65:350–357. https://api.semanticscholar.org/CorpusID:62453886
- Okunbor D, Sharma RK. Object-oriented software for galois field-based encryption. Int J Bus Strategy. 2022;22(1):5–15. doi: 10.18374/IJBS-22-1.1
- Krishnapriya PV, Smitha S. Image security using linear feedback shift register. Int J Innov Sci Res Tech. 2017;2. https://ijisrt.com/wp-content/uploads/2017/07/Image-Security-Using-Linear-Feedback-Shift-Register.pdf