ABSTRACT
This paper investigates the influence of transnational challenges and decision-making heuristics and biases on the implementation of risk assessment (RA) process in the context of Critical Infrastructure Protection (CIP). The investigation, which is based on a review of existing literature and a critical analysis of the ISO31000:2018 process, suggests that contemporary RA models and processes fail to adequately consider the domain-based characteristics of transnational Critical Infrastructure (CI) characteristics. They also fail to recognize the full extent of the human decision-making influence on the RA process itself, as well as the relative lack of homogeneity across assets, stakeholders, countries, paradigms, and people in transnational CI environments. The findings from this work provide a theoretical contribution towards a better understanding of the complexities introduced by the transnational nature of CIP and the effect of human decision-making. They can provide the impetus for further research in the fields of CIP and RA.
1. Introduction
The concept and importance of CI-acquired prominence in our societies during the last decades of the twentieth Century. The worldwide interest in the protection of CI was triggered by headlining events such as the attacks on New York City’s World Trade Center towers in February 1993, the 1994 cyber-attacks against US Air Force systems at Rome Labs, and the 2004 al Qaeda train attacks in Madrid, Spain (Renda & Haemmerli, Citation2010; Sachs, Citation2022). CIs are characterized by their complex structure and their strong impact on all aspects of society. The first formal definition of the concept appeared in 1996 with President Clinton’s Executive Order 13,010 (US Election Assistance Commission, Citation2017). Since then, CI-related definitions appear to be in a perpetual advancement and improvement mode. For the purpose of the discussion presented in this paper, an adapted version of the European Critical Infrastructure (ECI) definition, infused with asset-level specifics from the Patriot Act (US Congress, Citation2021), has been adopted. Specifically, CIs are defined as ’Systems and assets or part thereof, whether physical or virtual, located in any group of nations or states whose disruption or destruction would have a significant impact on at least two group member nations or states.’
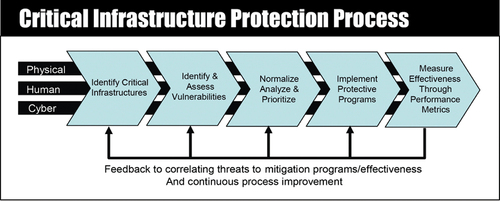
The risk management process which relates to the capacity of an entity to adequately prepare for and respond to serious incidents that involve the CI of a region or nation (European Council, Citation2008; White House, Citation1998) is commonly identified as the Critical Infrastructure Protection (CIP) Process. RA is at the heart of a CIP process given its role in the identification of threats, the assessment of vulnerabilities, and the evaluation of the impact on assets and systems (Giannopoulos, Filippini, & Schimmer, Citation2012). A characteristic example of such a process is the Risk Management Framework of the National Infrastructure Protection Plan (NIPP) developed by the Department of Homeland Security in the US, as depicted in (Homeland Security, Citationnd).
A multitude of RA methodologies have already been developed within the specific context of the CIP process; however, there is a significant differentiation in their scope of methodology, target audience, and domain of applicability. As a general framework, the established approach of the ISO31000 risk management framework (Rød, Lange, Theocharidou, et al., Citation2020) is being followed. This ‘gold standard’ (), which is widely accepted around the world by most G20 countries, provides the principles, an overarching framework, and the process for managing risk (Dali & Lajtha, Citation2012). The standard is not welcomed by everyone in the academic community, with critics citing the lack of a solid conceptual framework for risk management and the absence of scientific justification (Aven, Citation2017; Aven & Ylönen, Citation2019). Despite such criticisms, it forms the backbone of the EU/US RA processes (European Commission, Citation2019a).
Despite the use of standardized RA frameworks for CIP, there are frequent failures in their implementation with significant societal cost associated with them. Typical examples include the Yucca Mountain nuclear waste project which cost the US Government in excess of $13 billion US Dollars (Slovic, Layman, & Flynn, Citation1991), and the Bhopal disaster for which the death toll is estimated to be in the region of 16.000 deaths in addition to 558,125 injuries (Varma & Varma, Citation2005). These failures provide clear indications of the significant challenges faced during the implementation of the CIP process. For the purpose of the discussion and analysis presented in this paper, we can categorize these challenges into two main types:
Domain-based (CIP) challenges: The environment within which each RA process is taking place is unique in nature and is significantly affected by the domain characteristics of the CIP case considered. While these challenges vary greatly between each individual case, the EU region represents a prime example of the challenges which could potentially be faced: absence of a single hands-on government and the existence of a multitude of borders and legal frameworks (Skogstad, Citation2003) and looser controls on framework implementation and overview (Pursiainen & Rød, Citation2021). While specific attempts have been made to provide a harmonized framework for National Risk Assessments (NRA) at a European level (Theoharidou & Giannopoulos, Citation2015), these have not been able to produce significant results due to the aversion of member states of sharing sensitive information and the lack of an entity or process to serve as the sharing ‘medium’ (Yusta, Correa, & Lacal-Arántegui, Citation2011).
Horizontal RA methodological challenges and issues: There are known horizontal issues associated with the implementation of an RA process in any type of domain. Such issues may include the incomplete definition of the RA context and its objectives (Lyon & Hollcroft, Citation2012), the unsuitable choice of RA tools (Giannopoulos, Filippini, & Schimmer, Citation2012), the lack of objectivity (Hermansson, Citation2012), the potential failure to identify hazards and prioritize them effectively (Zio, Citation2016), and the inefficient communication between RA stakeholders (Andersson et al., Citation2020). Additional challenges include the varying perception of the severity of risk estimated by different individuals (Slovic et al., Citation1979), the inefficient interpretation of the information stemming from the RA process (Fairbrother et al., Citation1995), and the misalignment in the estimation of acceptance risk (Fischoff, Citation1984; Reid, Citation2000). On top of all these issues, a crucial horizontal challenge during the implementation of a generic RA process concerns the so-called ‘human angle’, in other words the decision-making aspects which critically affect the implementation of the CIP process and are intrinsically related to the previous challenges (Lazari, Citation2014).
The main aim of this paper is to provide a theoretical contribution towards a better understanding of some of the challenges faced during the implementation of the RA process within the context of the overall CIP process. It is evident that the critical analysis (in the appropriate breadth and depth) of all possible parameters which affects this process would be an impossible task within the context and the limitations of a single study. For this reason, our investigation explicitly targeted a specific challenge from each of the categories specified above, based on the following criteria:
A domain-based (CIP) challenge which is deemed by practitioners to be critical for the successful implementation of the RA process within the context of CIP (transnational challenges).
A horizontal challenge which is perceived in academic literature to be critical for the successful implementation of the RA process in any domain but has not been studied in detail within the context of the CIP domain (decision-making heuristics and biases).
An investigation of this kind, for these specific challenges, has not appeared in the CIP academic literature in the past, to the best of the authors’ knowledge. The particular objectives associated with our study are the following:
Objective 1: Investigate how transnational challenges affect the implementation of the RA process within the context of CIP.
Objective 2: Investigate how decision-making heuristics and biases affect the implementation of the RA process within the context of CIP.
Objective 3: Identify specific strengths, gaps, and opportunities in relation to the challenges identified in the previous objectives and formulate questions which will drive future research work in this domain.
A non-systematic narrative literature review of the academic and regulatory literature was conducted in order to elicit and analyze scientific and regulatory information regarding these challenges. The review is supported by a critical analysis of the ISO31000 process with regard to the way it addresses the specific challenges considered.
The rest of the paper is organized as follows: Section 2 overviews the methodology which was followed in order to carry out the study in consideration. Section 3 presents the findings of the study with regard to the way transnational challenges affect the implementation of the CIP RA process. The effect of decision-making heuristics and biases within the context of a CIP RA process is examined in Section 4. Section 5 summarizes and discusses the main results of our study with regard to its specific objectives and provides directions for future research on the topics considered. Finally, Section 6 presents the conclusions of the study.
2. Methodological considerations
A narrative review of academic and regulatory texts was carried out for the purpose of formulating a ‘… authoritative argument, based on the informed wisdom that is convincing to an audience of fellow experts’ (Greenhalgh, Thorne, & Malterud, Citation2018) which then facilitated the presentation of the evidence and how this was drawn upon to formulate the conclusions, synthesizing of the data from these documents (Bowen, Citation2009). Guidelines in (Greener, Citation2018) and (Hutten, Van Horn, Uzieblo, et al., Citation2022) were drawn upon. A structured search of documents relating to the identified research questions was carried out using Google Scholar with Boolean AND OR combinations of the search strings depicted in .
Table 1. Search Strings for the document search.
The search was conducted between September 2021 and December 2022 for English-only publications. No restrictions were applied in relation to the year of publication. Screened publications themselves were a secondary source of publications through their respective referenced work which was searched manually.
Inclusion was conditioned on at least one of the three main themes of transnational challenges, the human aspect of RA, and RA performance, be explicitly or implicitly referred to in the document. Document analysis steps of skimming, (in-depth) reading, and interpretation were pursued for the purpose of identifying excerpts and learning from the papers which was then be documented in support of answering the research questions identified earlier. The method was tested by exploring mechanisms for addressing interdependency-related risk across three critical national infrastructure sectors in Sweden (Sonesson, Johansson, & Cedergren, Citation2021).
The narrative literature review was supported by a critical analysis of the ‘gold standard’ ISO31000:2018 RA process with regard to the way it addresses the unique transnational and decision-making characteristics of a CIP project. The analysis was based on the critical examination of the provisions of the IS031000 RA framework, as these are described in the generic RA literature and viewed within the context of unique CIP transnational and decision-making challenges.
As this study is not experimental in nature, its limitations are mainly related to the known limitations of any literature review study. It only provides a snapshot of what has currently been published in academic and regulatory literature, thus it may not adequately reflect the perception and practices of CIP practitioners. In addition, although the study followed systematic elements in its search strategy, there is always a minor possibility that a relevant work has not been identified, especially if this was presented in a conference setting. Finally, as this study is not quantitative in nature, there is a subjective element in the interpretation and analysis of the findings, especially with regard to the critical analysis process.
3. Transnational challenges in CIP
3.1. Conceptualization of transnational challenges
There have been many attempts to conceptualize the characteristic of risk which relates to the crossing of national and other borders within the context of CI. The terms ‘transnational’ (Van der Vleuten & Lagendijk, Citation2010b), ‘cross-border’ (Borghetti, Marchionni, Gugiatti, et al., Citation2020; Coman, Citation2017), and ‘transboundary’ (Burgess, Citation2007; Fritzon, Ljungkvist, Boin, et al., Citation2007) have been extensively used in the literature for this purpose. Whilst the terms ‘transnational’ and ‘transboundary’ could be thought of as being equivalent to some extend (Cambridge on-line Dictionary, Citation2021), their use as part of the overall CIP process should be viewed through the following angles:
The term ‘transnational’ specifically alludes to a state or a nation’s boundaries which is consistent with the position expressed that a multinational environment, such as the case of the EU, would provide significant insights into the study.
It would appear that in so far as RA is concerned, the term ‘transboundary’ is often used to refer to environmental or public health risk and of resources crossing national boundaries, such as rivers, which are outside the scope of this paper (Linnerooth-Bayer & Sjostedt, Citation2010; Lidskog, Soneryd, Uggla, et al., Citation2009).
Based on the previous considerations, it can be said that the term ‘transnational’ constitutes a valid basis for guiding the discussion which follows, however, it should be stated that the alternative terms were also explicitly considered in our analysis, wherever they appeared in the literature in the context of the topic considered.
3.2. Transnational considerations in the CIP literature
In general, it has been specifically argued that Europe’s present-day vulnerabilities reside precisely in their transnational character (Högselius, Hommels, Kaijser, et al., Citation2013). Despite its recognized importance, the concept of transnational challenges within the context of RA for CIP has not attracted the attention of researchers to any significant degree (Pursiainen & Rød, Citation2021). Some examples include the EURAM model (Klaver, Luiijf, Nieuwenhuijs, et al., Citation2008), the EURACOM framework (CORDIS, Citation2011), and numerous multi-national CI-related crisis exercises run by EU and NATO (European Commission, Citation2016). Similarly, regulatory efforts to address transnational considerations through enhancing the comparability of National Risk Assessments in the EU have not become influential through effectively a failure of the endeavor itself (European Commission, Citation2022; Pursiainen & Kytömaa, Citation2023; Pursiainen & Rød, Citation2021; European Commission Citation2019b). Another such example is the effort to address the comparability issue between NRAs using the CRitical Infrastructures and Systems Risk and Resilience Assessment Methodology (CRISRRAM) model (Theocharidou & Giannopoulos, Citation2015), which does not seem to have attracted significant attention either.
It should be stated that the concept of transnational challenges is indeed frequently considered within the context of CI literature but not in a direct manner. In particular, the following CI areas of research are naturally related to transnational considerations:
Threats to CI from foreign adversaries (Center for Homeland Defense and Security, Citation2020; Department of Homeland Security, Citation2021; Hammond-Errey & Ray, Citation2021): This is a common consideration in CI papers relating to countries outside of the European space, more frequently the US, Australia, and other geographies with few, if any, nation state neighbors. In this case, transnational threats and risk relate to adversaries outside the respective country’s hinterland who aim to harm CI in some way.
Cyber threats which defy any concept of geography or border (Sofaer & Goodman, Citation2001; ENISA, Citation2021; Gaiser, Citation2018; Fischerkeller & Harknett, Citation2017): This body of work relates to cyber-type risk which is inherently transnational due to the interconnected, cross-border nature of the present-day information and communication technology infrastructure.
Threats against physical elements of CI which span across country boundaries (Sofaer & Goodman, Citation2001): Research work identified in this context is more frequently seen in relation to the EU or EU member states and other countries.
In the context of this paper, the term ‘transnationalism’ will broadly ‘refer to multiple ties and interactions linking people or in situations across the borders of nation-states’ (Vertovec, Citation1999, p. 447) with its meaning grounded upon the distinct conceptual premises of avenue of capital and the reconstruction of ‘place’ or locality. Surprisingly, though and despite the fact that transnationalism is a domain-based concept frequently associated with CIP projects, it is not directly addressed in published studies as an integral part of the CIP process. In particular, the review of the literature did not identify frameworks which explicitly address the existence of transnational dynamics and spatial infrastructure vulnerabilities during the implementation of the CIP process. This finding creates the need for further investigation and analysis with regard to the actual need of explicitly addressing transnationalism as part of the implementation of the CIP process, as well as the potential risk posed by its non-consideration. Fortunately, academic literature provides significant evidence on this topic, as this is discussed in the following sub-section.
3.2.1. Vulnerability
Discrepancy in the interpretation of vulnerability is not uncommon, as it has been showcased in the example of the ‘European Blackout’ case (Van der Vleuten & Lagendijk, Citation2010a, Citation2010b). Assigning an estimated value to vulnerability during the risk evaluation phase of the CIP process, especially in the transnational context, is very challenging before an actual breakdown takes place. Even then, the magnitude of the disruption is influenced by mitigation measures implemented before the event. The example of the contested vulnerability of electrical power generation in the EU has prompted increasing regulating powers for the EU on the pretext of economic and sustainability arguments. That said, regulation is not always the answer given the paradox of sometimes additional CI vulnerability being produced by the very measures implemented to reduce vulnerability in the first place (Disco & Lintsen, Citation1998; Van der Vleuten & Disco, Citation2004). The piecemeal linear approach of addressing vulnerabilities in isolation on the assumption that outcomes would be aggregatable has also been challenged (Birkmann, Feldmeyer, McMillan, et al., Citation2021). It is proposed that the strengthening of transboundary approaches for the reduction of vulnerability in recognition of the emergence of spatial statistical hotspots as an outcome of a group of hazards rather than the influence of single hazards and yet national approaches, at least in Europe, are an outcome of the normal practice of positioning of individual countries within vulnerability rankings which, in turn, is linked to the linear RA models in use (Theocharidou & Giannopoulos, Citation2015). This realization discredits any RA process delving beyond the borders of a single nation if it assumes that the outcomes of a piecemeal approach to risk and vulnerability assessment could be aggregatable, rendering transnational consolidation of RAs for the purpose of CIP improbable.
3.2.2. Interdependence
The terms interdependency and dependency are often used interchangeably in the CIP literature. Dependency ‘ … is a uni-directional relationship of two infrastructures through which the state of the depending infrastructure is influenced by or is correlated to the state of the other’ and interdependency is a ’ … mutually reliant relationship between entities (objects, individuals, or groups)’ (Department of Homeland Security, Citation2013; Luiijf & Klaver, Citation2021; Rinaldi, Peerenboom, & Kelly, Citation2001). Both terms will be used as mentioned in the respective references for the sake of consistency.
CIs are complex, interdependent systems where a potential failure propagating among infrastructures may affect the entirety of the network. While it has been suggested that an indeterminate risk should be accepted by governments in such cases (Clemente, Citation2013), the CI literature is rich with attempts to pursue models and processes that address the challenge of adequately managing CI interdependency. These attempts are overwhelmingly considering the interdependency challenge solely within national borders. A typical US example is the early pioneering work of Rinaldi, Peerenboom, and Kelly (Citation2001) who introduced the concept of infrastructures as complex adaptive systems and highlighted the challenges in developing, applying, and validating modeling and simulation methodologies for infrastructure interdependency analysis. The potential of propagation of failure of CIs and the associated cascading effects throughout the network was also discussed (Eusgeld, Nan, & Dietz, Citation2011); however, it is evident that such cascade effects may extend beyond the geographical borders of a nation. More recent work which takes up the challenge of looking at the issue in much broader terms ran an analysis of a unique multinational database resource of CI and Critical Information Infrastructure (CII) threats, failures, disruptions, and lost infrastructure between 2004 and 2010 (Van Eeten, Nieuwenhuijs, Luiijf, et al., Citation2011) and again for data collected between 2004 and 2018 (Luiijf & Klaver, Citation2021). Outcomes were consistent in that the analysis of trends, dependencies and common cause failure phenomena, and the improved understanding of other CI/CII related phenomena in both of these studies dictates that the pervasive web of CI/CII dependencies has the potential to cause significant damage and societal disruption and may be challenging to secure and govern (Luiijf & Klaver, Citation2021). Given that the research work in a transnational context would be hindered by methodological considerations such as the comparability of the results, the ambiguity of terms used in the various geographies and respective sectors, and the need for dependency analysis (Theocharidou & Giannopoulos, Citation2015), effective RA for a transnational system is bound even more challenging.
3.2.3. Governance
Given the complexity of CI projects, it is natural to assume that the management of a transnational CI from within national ‘silos’ can potentially introduce governance issues. Moreover, the actual delivery of governance for CI could be in doubt when national RAs are not aligned and coordinated. It is suggested that coordinated governance across a transnational CI project will face challenges if it is pursued only through the respective ‘national’ tools of each country. The EU is highlighted as a characteristic example of such challenges (Bossong, Citation2014). In particular, it is argued that despite the advent of sector-specific DGs (General Directorates), and the support of the Joint Research Center (JRC), its very own research unit, CI governance remains fragmented. It was suggested that these challenges can be attributed to the difficulties of managing cross-sector policy programs and the significant harmonization costs associated with the high level of regulatory and institutional diversity (May & Koski, Citation2013). On the project level, transnational Public Private Partnerships (PPP) remain the more prominent platform for financing and delivering CI projects although the ‘ … phenomena … range from loose cooperation forms to legally binding contracts for the implementation of specific projects’ (Schäferhoff, Campe, & Kaan, Citation2009, p. 6). Still, issues related to responsibilities, risk, or authorities in the partnership, differences between the partners in working methods, as well as lack of commitment from the partners, generate significant challenges to the management of CI projects (Yu, Chan, Chen, et al., Citation2018).
Summarizing, the analysis of the literature suggests that transnationalism can have a strong impact on the implementation of the RA process within the context of CIP, especially in terms of asset vulnerability, interdependency between elements and functions of a project across national boundaries, and governance, or absence of it thereof, in relation to the management of RA transnational elements. The implications of this finding will be further discussed in section 5 of this paper.
3.3. Influence of transnationalism in the CIP process
The need for the explicit consideration of transnationalism parameters as part of the CIP process is being extensively emphasized in academic literature. In particular, it has been argued that, within the context of CIP, the concept of transnationalism influences the implementation of RA within the context of the CIP process on a number of levels. Particular focus is given to the dimensions of vulnerability, interdependency, and governance.
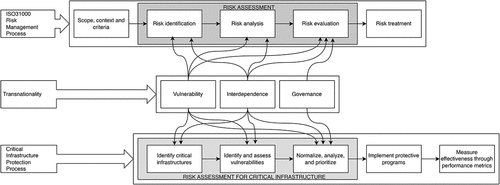
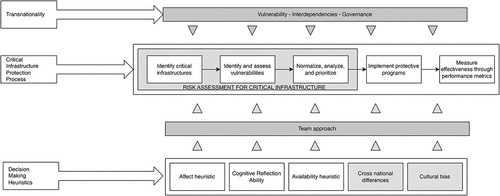
provides the graphical framework for the facilitation of discussion regarding the potential effects of transnationalism within the context of the CIP process. In particular, the figure illustrates both the generic ‘gold standard’ ISO31000:2018 Risk Management process, as well as a generic implementation framework of the CIP process. In between them, the main transnationalism dimensions which are the focus of our discussion are showcased. Association arrows have been drawn between each of these aspects and the corresponding stages which can potentially be affected by them during the implementation of the ISO31000:2018 process (and consequently during the implementation of the CIP process), according to the academic literature.
indicates that there is a strong association between the transnational dimensions in consideration and all stages of the RA implementation process within the context of the CIP process. The nature of this association is discussed in detail in the following paragraphs:
4. Decision-making challenges in CIP
4.1. Conceptualization of risk perception and of decision-making heuristics and biases
The Society for Risk Analysis (SRA) defines risk perception as a person’s subjective judgement or appraisal of risk (Aven et al., 2008). The deviation between real risk and the way it is perceived is caused by a range of affective, cognitive, contextual, and individual factors (Aven et al., Citation2018a). Three of these four factors stem out of the qualities of the individual. Affective factors include emotions and feelings of the person in question, while cognitive factors can include media coverage and the framing of risk information. Individual factors relate to the individual’s previous experience, age, and personality traits, while contextual factors relate to the way information is framed and the way alternative information sources are accessed.
It has been suggested that perception of risk resides within individuals sometimes as a feeling and in other instances as an appreciation of risk which is the outcome of deliberate analysis (Slovic, Citation2020). The assertion is that they should be looked upon as the two sides of the same coin irrespective of the disparity they represent. The same individual is also capable of all but rational decisions and judgements as influenced by their own biases and prejudices. Early research in risk perception showed that the more profound indication of risk for any given hazard is the degree to which it evokes feelings of dread and that perceived risk and benefit are inversely correlated (Slovic, Fischhoff, & Lichtenstein, Citation1982). Moreover, work on how individuals think, described as slow and fast modes, was subsequently shown to be indispensable to rational decision-making (Slovic, Finucane, Peters, et al., Citation2004, Kahneman, 2011 as referenced in; Slovic, Citation2020, p. 3). These decisions are said to be influenced by heuristics (Slovic, Finucane, Peters, et al., Citation2004).
Heuristics can be defined as the shortcuts to task complexity in judgement, and biases as the space between normative and heuristically driven behavior (Kahneman & Tversky, Citation1982). They are dis-optimal, imperfect, and irrational approaches to problem solving which can, nonetheless, speed up the process of finding a satisfactory solution. Heuristics have been linked to cognitive biases (Tversky & Kahneman, Citation1974), while pre-event predictions of behavior requiring formal modelling of the decision process are proposed (Gigerenzer & Todd, Citation1999). However, much as heuristics are neither always accurate nor driven by logic, they are often enough to satisfy a need and often seem to work (Mousavi & Gigerenzer, Citation2014). In fact, it has been shown that at least for some business situations, heuristic decision-making can be effective if some information is purposely ignored with less proving to be more under uncertainty when knowledge takes precedence over information abundance (Mousavi & Gigerenzer, Citation2014).
Focusing on the implementation of RA within the context of the CIP process in particular, the onus is frequently on the RA professional, the cornerstone of the RA process, whose input is prevalent at all CIP activity levels (Poljanšek, Casajus Valles, Marin Ferrer, et al., Citation2019) and whose judgement may be led astray by heuristic’s ability to ‘lubricate reason’ (Slovic, Finucane, Peters, et al., Citation2007). It has been argued that the RA professional has to make decisions during the CIP process lacking the tools and processes which can identify and address the extent of systems links across national borders and into other sectors (Pidgeon & O’Leary, Citation2000). The following subsection examines the use of decision-making heuristics by the RA professional within the context of the CIP process, as this has been discussed in academic literature.
4.2. Decision-making heuristics and biases in the CIP literature
As in the case for the transnationalism concept, the review of the literature provides only a limited number of direct references related to the effect of RA decision-making heuristics and biases within the specific context of the CIP process. Research work on non-CIP-specific human decision-making heuristics and biases is slightly more populus albeit with more focus on risk perception rather than RA. However, given that the ‘gold standard’ RA methodology employed during CIP is the ISO 31,000:2018 risk management process (as already discussed in section 3 of this paper), the set of decision-making heuristics which are reported in the literature to be employed during the latter process are (in principle) applicable to the CIP process as well. A brief description of these heuristics and biases, as well as their potential impact on the RA process within the context of CIP, is provided in the following paragraphs:
The Affect Heuristic: The affect heuristic is defined as a feeling state such as happiness or sadness but also as goodness or badness, assigned to a stimulus experienced by people (Slovic, Citation2000). It is considered to be a prominent heuristic in relation to risk (Tversky & Kahneman, Citation1974). There is scientific evidence which showcases the direct influence of the affect heuristic on risk perception (Van Schaik, Renaud, Wilson, et al., Citation2020) and its impact on affective information to perceived-risk judgments (Pachur et al., 2012). More importantly (for the scope of this paper) it has been specifically argued in the academic literature that the affect (as well as the availability heuristic discussed later) can directly influence the CIP RA process by being a source of the so-called ‘blind-spots’ which could trigger catastrophe across CI systems (Blackwell, Tolone, Lee, et al., Citation2009). Interestingly, the affect heuristic might also have an effect possible team-level discussions on the risk level, which constitutes a typical case for large projects. This effect will be discussed in more detail in the following sub-sections.
Availability Heuristic: Individuals use the heuristic of availability, a mental shortcut that bases decisions on immediate examples that come to mind, to estimate the frequency of an event or the likelihood of its occurrence by ‘the ease with which relevant instances or associations come to mind’ (Tversky & Kahneman, Citation1973). The availability heuristic can have a significant effect on the risk practitioner’s perception of the likelihood of an event (Slovic et al., Citation1981). As such, it can influence RA activities in general, and the RA activities within the context of the CIP process in process, where the team decision-making element is likely to feature (Blackwell et al., Citation2009; Slovic et al., Citation1981). The availability heuristic has been reported to explain differences in the perception of risk across groups, cultures, and even nations effectively. This finding bears additional relevance for CIP given its transnational nature (Sunstein, Citation2005).
Cognitive Reflection Ability: Cognitive reflection relates to the ability or disposition to reflect on a question and resist an automatic response (Frederick, Citation2005; Toplak, West, & Stanovich, Citation2011). As such, cognitive reflection can have a potential effect to the entirety of the RA process within the context of CIP, from threat identification to the formulation of mitigation strategies. Risk professionals can be biased by the context, and the way information is presented (Berger, Citation2015). In addition, the strength of the inverse correlation is tied to individual cognitive abilities, with cognitive reflection ability at the forefront (Skagerlund, Forsblad, Slovic, et al., Citation2020). However, there are no direct references in the academic literature with regard to the implications of cognitive reflection ability for RA professionals within the CIP context.
Cross-cultural Differences and Cultural Bias: While these concepts are not heuristics in their own right, their transnational nature can introduce biases which extend beyond the confines of a single nation. In particular, differences in risk preference between nations are associated with national culture differences in their peoples’ respective perception of risk rather than their attitudes towards perceived risk (Weber & Hsee, Citation1998). Studies have shown that in addition to cross-cultural disparities between professional groups within a country, there are also considerable cross-national differences in how risk is perceived (Rohrmann, Citation2000). In addition, a wide range of basic psychological processes have been known to be influenced by culture including the likelihood of the fundamental attribution error and probabilistic thinking (Weber & Hsee, Citation1998). It is therefore evident that with the multitude of national stakeholders in each of the facets of a CIP project, maintaining consistency in RA evaluations as well as a uniform risk perception across regions and states constitutes a serious challenge. Despite this, such challenges have not been considered/examined in RA literature in the context of CIP.
Summarizing, while there exists considerable literature on the effect of decision-making heuristics and biases in the generic RA process, their implication has not been adequately examined within the specific context of CIP. In particular, the review of the literature did not identify works which critically analyze the use of decision-making heuristics within the complex, transnational environment of a CIP process, as this has been unveiled in the discussion of Section 4.1. Therefore, further investigation and analysis are necessary with regard to the potential influence of decision-making heuristics and biases as part of the implementation of the CIP process, in particular. To this end, the following subsections discuss two types of decision-making dimensions which can potentially emerge during the implementation of RA within the context of CIP. The first relates to the influence of decision-making heuristics on the level of an individual professional’s risk perception (Aven et al., Citation2018a; Aven, Ben-Haim, Andersen, et al., Citation2018; Slovic, Citation2020) and how this may affect decisions made in the context of RA for CIP. The second relates to how a team-based RA may be influenced in the context of these decision-making heuristics (Slovic, Fischhoff, & Lichtenstein, Citation1982; Slovic et al., Citation2004), viewed within the context of RA professionals employed in mass for a CIP project.
4.3. Influence of decision-making heuristics in the cip process (individual level)
Human input is apparent in all phases of the CIP process (), including the actual RA activity, the training to build the necessary RA expertise, including the evolution of requirements stemming from CI system adaptivity and the assessment of relevant capabilities. The identification and selection of the specific CI to be included in any analysis and the very definition of what constitutes a CI are looked upon differently between policymakers and operators which emphasizes the value of the individual in the process (Poljanšek et al., Citation2019).
Human input is apparent in all phases of the RA process and beyond; the actual RA activity, the training to build the necessary RA expertise, including the evolution of requirements stemming from CI system adaptivity and the assessment of said capabilities.
The practitioner is effectively the cornerstone of the RA process within the context of CIP. Knowledge and expertise in this respect needs to be built. Poljanšek, Casajus Valles, Marin Ferrer, et al. (Citation2019) have shown that continuously assessing one’s risk management capability can be a significant driver to the development of those capabilities. One common characteristic of CI is that they are complex adaptive systems (CAS) in that their many constituent elements affect the overall system as a result of the respective learning processes over time; transformers and battery systems degrade over time, pipelines rust and age, the operating team improves in their adaptation and ability to manage the system over time (Rinaldi, Peerenboom, & Kelly, Citation2001). The importance of this in the context of the paper is the need for individuals engaged in RA for CIP to recognize in their decision-making activities the inherent nature of CI and their emergent behaviors in this respect in terms of risk and its assessment thereof, but also in terms of possible interdependencies between systems and elements of infrastructure.
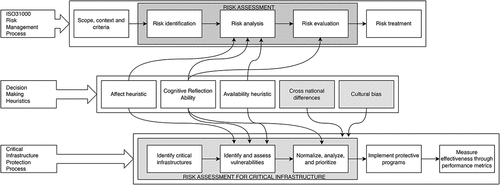
provides a graphical framework of an individual’s decision-making aspects as these are perceived during the implementation of the ‘gold standard’ ISO31000:2018 RA process and the RA process within the context of the CIP. Looking deeper into this framework, based on what has been published in academic literature, it can be said that CIP-specific RA models in use are not unlike generic RA models as attested by the convergence in their linear approach to process, and their likeness to the ISO 31,000:2018 standard. In this respect, decision-making heuristics and biases particular to RA are also relevant to CIP. Such associations can be found between the process of risk perception and the affect and availability heuristics (Pachur, Hertwig, & Steinmann, Citation2012; Sunstein, Citation2005; Van Schaik, Renaud, Wilson, et al., Citation2020), between the entire RA process and the cognitive reflection ability (Berger, Citation2015; Skagerlund, Forsblad, Slovic, et al., Citation2020), and between the perceived severity of risk and the cross-national differences and cultural biases (Bontempo, Bottom, & Weber, Citation1997; Jasanoff, Citation1991; Sunstein, Citation2005).
However, it is of critical importance to state that the unique nature of a CI project introduces additional challenges to the implementation of the RA process in relation to the characteristics in consideration. This relates to the increased complexity of CI projects in relation to non-CI projects (Ulusan, Ergun, & He, Citation2018), even if not transnational, which requires an enlarged pool of RA professionals to cover the increased scope which, in turn, introduces additional heuristic decision-making challenges. In addition, the transnational nature of CI projects (Heino, Takala, Jukarainen, et al., Citation2019), which necessitates the ability to define issues across geographical boundaries, can be the source of an enlarged scope for RA with additional risk professionals contributing from different geographies and countries, a multi-faceted regulatory framework, and an increased stakeholder population. This will invariably lead to additional scope and complexity, through sheer size, in identifying and addressing decision-making heuristics and biases, transnational vulnerabilities, and regulation streamlining and coordination issues, such as reliability and safety standards, across the larger footprint of the project (Roe & Schulman, Citation2018).
4.4. Influence of decision-making heuristics in the cip process (team level)
The team-based approach to decision-making has been suggested as a remedy to decision-making heuristic deficiencies as it may attenuate cognitive biases (Cianni & Wnuck, Citation1997). However, it has been argued that teams might also be inclined towards similar information-processing biases (Schwenk, Citation1986). Moreover, it is reported that these teams often use the same ‘rules of thumb’ individuals use to process information, invariably leading to similar errors in judgement (Houghton, Simon, Aquino, et al., Citation2000).
The RA literature predominantly discusses the optimal formation of a decision-making team rather than its decision-making characteristics, including the existence of heuristics and biases. A typical example is the proposed ‘high-functioning risk team’ approach, which has actually been suggested for the case of CIP projects, without providing any further details on the suitability of this approach for the particular domain (Baggett & Stout, Citation2022). Alternative team-based approaches which can potentially be relevant to the CIP process include the ‘unity of effort’ approach (Baggett & Stout, Citation2022; Stockton & Roberts, Citation2008), which constitutes one of the key tenants of RA, ensuring a consistent approach by all stakeholders for maximum effectiveness. This approach calls for the selection of a team from both internal and external stakeholders, supervisory, and line, who would need to be trained in RA methods. Another example is the ‘red-team’ approach to critical operations (Veland & Aven, Citation2015) where the RA is carried out by two different teams and where the external team subsequently challenges the self-evaluation of the internal analyst team, and both eventually work together for a final consensus, while group decision-making sessions using the Delphi method and sources of knowledge, such as risk-event histories, during the RA process are also proposed (Yildiz, Dikmen, & Birgonul, Citation2014).
Based on the previous, provides a graphical framework of the team’s decision-making aspects as these are perceived during the implementation of the RA process within the context of the CIP. What can be deduced from this framework is that all team decision-making approaches discussed above fail to address the added complexity and enlarged scope which CIP brings about. Specifically, beyond the actual composition of the decision-making team, the sheer size of a CI project introduces added complexity (Heino, Takala, Jukarainen, et al., Citation2019). Transnational-driven issues of vulnerability, interdependence and governance and decision-making heuristics were shown to influence the CIP process, with the latter being additionally challenged by a transnational-team or team-of-teams approach to RA, given the much wider scope of CI (Ulusan, Ergun, & He, Citation2018) and their inherent structural and dynamic complexities (Zio, Citation2016).
Summarizing, much as there are not many studies discussing and analyzing the team-level decision-making characteristics of the RA process within the context of CIP, there are advocates of the team-based approach in the literature, as seen in this section. However, what is advocated remains at a high-level and does not specifically prescribe how the team will function together nor how practitioner characteristics will be prevented from influencing local and indeed regional RA work.
5. Discussion
The concept and importance of CI, as well as its protection (CIP), acquired prominence in our societies during the last decades of the twentieth Century following numerous high-profile terrorist attacks (Renda & Haemmerli, Citation2010; Sachs, Citation2022). RA is at the heart of this CIP risk management process which relates to the capacity of an entity to adequately prepare for and respond to such serious incidents. The information presented and the analysis of the previous sections indicates that the RA models employed within the context of CIP-specific are similar to generic RA models as they converge in their linear approach to process and are largely based on the ISO 31,000:2018 ‘gold standard’.
Our study investigated whether this standardized approach would actually ‘fit’ for the case of CIP, or if there are CIP-specific considerations (‘challenges’) which are potentially not adequately addressed by the use of the ‘gold standard’ approach to the RA implementation within the context of CIP. As discussed in the introductory section, two particular ‘challenges’ were investigated for their influence on the implementation of the CIP RA process. In particular, the influence of the transnationalism dimension, which is a CIP-specific challenge, and also the use of decision-making heuristics and biases, which is a horizontal RA challenge. A narrative literature review was employed in order to identify relevant information which has been published in academic literature. Given the limited amount of research which has been conducted on these topics (from the CIP perspective), our study also considered academic research works from the generic RA literature and showcased how the CIP process can potentially be affected by the two main challenges in consideration.
Given the objectives of the study which were presented in the introductory section of this paper, the main findings of the study are presented below:
Objective 1: Investigate how the concept of transnationalism currently affects the implementation of the RA process within the context of CIP.
Conceptualizing transnationalism in its own merit is not a straightforward task, as evidenced by the discussion in section 3.1. It does, however, constitute an extensively researched notion albeit in isolation of the RA practitioner, employed by practitioners within the context of CIP due to its perceived importance. For this reason, the apparent lack of studies which explicitly consider transnationalism as an integral part of the CIP RA process specifically and have developed appropriate tools to this end at the RA practitioner level, was a rather unexpected, but a very important finding of our study.
Naturally, the study extended to the potential influence of some principal dimensions of transnationalism on the RA process within the context of CIP. In particular, the dimensions of vulnerability, interdependency, and governance were investigated, based on what has been published in the generic RA literature, as well as on the theoretical foundations of the CIP process. What was evidenced is that the transnational complexity of CIP projects can potentially render the use of generic linear RA models ineffective within the context of CIP. In particular:
Vulnerability assessments in a transnational setting become very complex, rendering tasks such as the aggregation of risk in some cross-border or cross-regional cases close to impossible.
The interdependencies across multiple assets and borders, as well as the possible propagation of failure of CI and the associated cascading effects become even more difficult to fathom, document, and subsequently manage.
Governance issues related to responsibilities, risk, or authorities in the partnership of CI, generate significant challenges to their management but also increase the cost of harmonization given the higher level of regulatory and institutional diversity.
Finally, it should be noted that the previous findings should also be viewed within the context of the added risk and difficulties introduced by PPP structures, a prominent platform for delivering CI, and by the increase of the number of CI stakeholders from across different national and international boundaries.
Objective 2: Investigate how various decision-making heuristics and biases currently affect the implementation of the RA process within the context of CIP.
The fact that human decision-making (both on the individual and the team level) is affected by heuristics and biases has been well discussed in academic literature. In the domain of RA in particular, the impact of decision-making heuristics on the professional’s perception of risk is a significant consideration. The limited literature discussing the effect of decision-making heuristics and biases in RA within the context of the CIP process was therefore the second unexpected and important finding of this study.
Naturally, a further investigation was conducted on the potential influence of specific decision-making heuristics and biases on the CIP RA process (both from the individual and the team perspective), based on the findings of the generic RA literature and the theoretical foundations of the CIP process. The heuristics and biases investigated were the affect and availability heuristics, the cognitive reflection ability, as well as the cross-national and cultural differences. While it became evident from our investigation that these heuristics and biases are naturally relevant to the implementation of the entire RA process within the context of the CIP, our study also suggests that their influence on the CIP RA process should be viewed within the following context:
CI is complex adaptive systems; therefore, the inherent nature of CI and their respective emergent behaviors can have a significant influence on the decision-making activities during the CIP RA process.
The cross-national differences and the cultural biases are amplified within the context of a transnational CIP project, potentially affecting the perceived severity of risk across borders.
The CIP domain-specific concept of transnationalism (which has been discussed in detail in section 3 of this document) provides an additional layer of complexity in addressing decision-making heuristics and biases of the individual decision-maker.
While generic RA team-based decision-making approaches which appear in the literature are potentially applicable to the CIP RA process, these can be challenged by the much wider scope of a CI project (in relation to simple generic RA processes) and the well-documented structural and dynamic complexities of a CIP project and the consistency of CIP RA evaluations.
Based on the previous, one of the most interesting findings of our study is related to the fact that the approach to the two ‘challenges’ originally selected for independent investigation (transnationalism and decision-making heuristics and biases) ‘converge’ in their linear approach to process during the analysis of the RA CIP literature. This finding showcases the need for further investigation of the topics considered, as this is discussed in the following paragraph.
Objective 3: Identify specific gaps and opportunities in relation to the challenges outlined in the previous objectives and formulate questions which will drive future research work in this domain.
The findings of this study which were discussed within the context of study objectives 1 and 2 provide a convenient basis for the identification of the main gaps which currently exist in the literature. In general, it can be said that academic studies related to the analysis of the overall RA process within the specific context of CIP have been limited. Naturally, this means that studies for specific RA considerations within the context of CIP, such as transnational considerations and decision-making heuristics and biases would also be limited. However, what was rather unexpected (as discussed in the previous paragraphs) was not only the fact that the number of studies on these particular considerations was very low but also the observation that the limited attempts which have appeared in the literature have not seemed to trigger the implementation of further research work on their analysis. This gap is especially important when viewed under the analysis presented in this paper (sections 3.3 and 4.3), which showcased how the CIP RA process can potentially be affected by these unique challenges.
Looking into the gaps identified for the transnationalism challenge in particular, it can be said that there is a need to analyze in depth the process of aggregating risk across CI during a vulnerability assessment of a transnational CIP project. Current RA models do not accommodate this calculation, and it is not readily obvious how this process should be performed. At the same time, there seem to be no models available which allow the assessment of cascading effects of a CI failure on transnational, interdependent CIP projects. Last but not least, there is a gap in the investigation of the effects of governance issues on the implementation of the CIP RA process in transnational projects.
Challenges and issues have also been identified based on the analysis of decision-making heuristics and biases during the implementation of the CIP RA process. The horizontal RA nature of these challenges means that models and procedures do exist in the literature which provide solid frameworks for their analysis. However, once the specific characteristics which underline the unique nature of the CIP process are considered (complexity of the adaptive system, transnationalism), our analysis showcases that current approaches might be ineffective in modelling and managing the individual and team-based decision-making characteristics of the risk assessor in CIP projects. The gap becomes especially evident in the case of the generic team-based RA decision-making approaches which, as reported in the literature, do not readily accommodate the characteristics of complex, transnational CIP projects.
Validation through real-world examples of the proposed failure of the RA process to capture the realities of transnational CI projects and to recognize the full extent of the human decision-making influence on the RA process itself can only be the outcome of thorough analysis of numerous case studies. Whilst this cannot be possible in a paper of this nature given the restrictive word-count limitation, two CI examples portray signs of these traits.
The first example relates to the 2013 terrorist attack at the Statoil In Amenas gas facility in Algeria. An investigation into the attack (Equinor, Citation2013) whose purpose was to clarify the chain of events and to facilitate learning and further improvements within risk assessment, security, and emergency preparedness revealed a number of security vulnerabilities and shortcomings stemming from a combination of a number of factors including the project’s transnational nature. Concerns were raised in reference to the scope of the risk assessment at the terminal for failing to capture and consider the significance of regional geopolitical events and their potential impact (Institute of Strategic Risk Management, Citation2023). Risk Assessment activity was ‘split’ between Statoil’s Algiers office with emergency response plans influenced by the experience in Egypt and Libya, the London office, and company headquarters in Norway with stakeholders spread across geographies, businesses, and functions (Statoil, Citation2013). In fact, Lambrechts and Blomquist (Citation2017) suggest that Statoil lacked a holistic approach to risk management, with political risk seen as a public relations issue and security risk normally outsourced.
The second relates to the BTC (Baku-Tbilisi-Ceyhan) pipeline and the RA failings that supposedly led to the attack in 2008, although the accuracy of the cyber-attack report itself has been questioned (Lee, Citation2015). These failings suggest that actual security infrastructure and the socio-political risks may not have been adequately addressed. This may be an outcome of the transnational nature of the project which led to differing levels of activity at the national, tri-party, and regional levels for delivering protection (Starr & Cornell, Citation2005), non-aligned regional and local cooperation fora, and ad hoc geographical security alliances beyond the tri-party organization involving subsets of the BTC consortium state players and other regional states. Furthermore, even the language barriers at the risk assessment practitioner level may have contributed as well (Kogan, Citation2014) in addition to decision-making biases which have contributed to disasters in the past like the Challenger Space Shuttle Disaster in 1986 through confirmation bias which allowed launching during suboptimal temperatures (Murata, Nakamura, & Karwowski, Citation2015), Hurricane Katrina in 2005 where optimistic bias was a major contributing factor to inadequate response (Trumbo, Lueck, Marlatt, et al., Citation2011), and the Global Financial Crisis in 2008 where confirmation biases led to the underestimation of the risks (Shefrin, Citation2015). The previous discussion provides the basis for the formulation of a number of fundamental research questions on the implementation of RA within the context of a CIP process. These questions can potentially be investigated through future research activities on the topics considered. In particular:
How do CIP risk assessors perceive the applicability and relevance of the generic ISO31000 ‘gold standard’ RA process to the implementation of the CIP RA process?
How are CIP risk assessors influenced by transnationalism considerations (including vulnerability, interdependence, and governance) during the implementation of their tasks within the context of a CIP process?
How are CIP risk assessors influenced by decision-making heuristics and biases during the implementation of their tasks within the context of a CIP process?
How do CIP risk assessors perceive the applicability and relevance of generic team-based decision-making approaches to the implementation of the CIP RA process?
How can RA tasks which are implemented within the context of a CIP process be improved in order to explicitly address the unique characteristics of CI?
The development of research designs which would investigate the practitioners’ perception of the RA implementation within the context of a CIP process can provide the basis for addressing these questions. The authors of this paper are committed to further investigating this topic.
6. Conclusions
The main aim of this paper was to provide a theoretical contribution towards a better understanding of some of the unique challenges faced during the implementation of RA within the context of a CIP process. In particular, the influence of transnational considerations as well as of decision-making heuristics and biases was investigated. Our study was primarily based on the use of a non-systematic, narrative literature review on the implementation of RA tasks in CIP projects, which discussed existing works that discuss the challenges of transnationalism and decision-making heuristics and biases. The review was supported by a critical analysis of the implementation generic ‘gold standard’ RA process, which focused on investigating how this process addresses the specific CIP challenges in consideration.
Our study showcased that the implementation of RA within the context of CIP processes has not been adequately addressed. In particular, not only is the number of publications explicitly discussing the topic limited but also, as showcased by our critical analysis, the implementation of the generic ‘gold standard’ RA process fails to capture the realities of transnational CI projects and to recognize the full extent of the human decision-making influence on the RA process itself.
Our study suggests that the lack of homogeneity across assets, stakeholders, countries, paradigms, and people in transnational CIP environments challenges the existing generic RA processes. An improved, domain-specific RA process within the context of CIP, can potentially provide the framework for improved protection of CI. Nevertheless, it is evident that additional research work is necessary in order to better understand the challenges considered.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Data availability statement
Data sharing are not applicable to this article as no new data were created or analyzed in this study.
Additional information
Notes on contributors
Michalis Papamichael
Michalis Papamichael was born in Larnaca, Cyprus, in 1964. is a PhD Candidate in the Occupational Safety and Health Program at the European University Cyprus. He has over 32 years’ experience in the entirety of oil and gas value chain (upstream, midstream, and downstream) in regional roles of increasing accountability in the engineering, business, security, emergency management, and risk management context in Europe, the UK, and the Eastern Mediterranean. In his current role, he is the regional Security and Emergency Response Manager for an oil and gas major and a member of the company’s Global Corporate Emergency Response Team. Michalis holds a BSc in Electrical Engineering from Brown University, USA (1988), an MBA from Brunel University, UK (1997), and an MSc in Security and Risk Management from the University of Leicester, UK (2014). He holds certifications in the Incident Command System (now part of the National Incident Management System [NIMS] in the US), Kidnap for Ransom incident management, the management of major emergencies including oil spill management, International Ship and Port Facility Security (ISPS) Code at a Vessel, Company, and Facility security level, Security Consultancy, Business Continuity and Resilience, Intelligence Analysis, Open-source intelligence (OSINT) analysis, and investigations. He is an Honorary Research Fellow of the European University, Cyprus, and the co-chair of the OSAC (Overseas Security Advisory Council of the US State Department) Cyprus chapter.
Christos Dimopoulos
Christos Dimopoulos was born in Athens in May 1973. Christos is an Associate Professor of Computer Science & Engineering, and co-Director of the Centre of Excellence in Risk and Decision Sciences (CERIDES). He received his BSc degree in Automation from the Technological Educational Institute (TEI) of Piraeus. He received both his MSc and PhD degrees in Control Engineering from the University of Sheffield. He is a multidisciplinary researcher and practitioner with a significant focus in the area of Disaster Management. His research accomplishments include a considerable number of refereed articles and book chapters. In 2002, he received the ‘Outstanding Paper of the Year Award’ by the Neural Networks Council of IEEE. He is currently participating (and has participated in the past) as project coordinator, principal investigator and research collaborator in numerous European and Cypriot-level research projects. He has also served as the Scientific Coordinator and Head Evaluator in multiple Civil Protection Full-Scale Exercises funded by DG-ECHO. He is the recipient of an Honorary Award by the Cyprus Environmental Commissioner for providing services to the Republic of Cyprus towards achieving its Environmental Targets.
George Boustras
Georgios Boustras was born in Athens in May 1973. George is a Professor in Risk Assessment at European University Cyprus, Director of the Centre of Risk and Decision Sciences (CERIDES - Excellence in Innovation and Technology), Visiting Researcher at the National Observatory of Athens and Visiting Professor at University of Haifa. He is a Member of the EU Mission: Adaptation to Climate Change. George is Editor-in-Chief of Safety Science (Elsevier, IF 6.392) and Member of the Editorial Board of Fire Technology (Springer Nature) and the International Journal of Critical Infrastructure Protection (Inderscience). He (co)supervises five PhD students; six of his students are now PhDs.
References
- Andersson, M. G., Elving, J., Nordkvist, E., Urdl, M., Engblom, L., Mader, A., Ali, B., Kowalczyk, J., Lahrssen‐Wiederholt, M., Tuominen, P., Joutsen, S., Suomi, J., Mikkelä, A., Hinkka, N., Siekkinen, K.-M., der Fels‐Klerx, H. J. V., van den Borne, B., & Ali, B. (2020). Communication inside Risk Assessment and Risk Management (COMRISK). EFSA Supporting Publications, 17(7), 1891E. https://doi.org/10.2903/sp.efsa.2020.EN-1891
- Aven, T. (2017). The flaws of the ISO 31000 conceptualisation of risk. Proceedings of the Institution of Mechanical Engineers, Part O: Journal of Risk and Reliability, 231(5), 467–468. https://doi.org/10.1177/1748006X17690672
- Aven, T., Andersen, H. B., Cox, T., Droguett, E. L., Greenbergm M., Guikema, S., Kröger, W., McComas, K., Renn, O., M. Thompson, K., & Zio, Eet al. (2018a). Risk Analysis: Fundamental Principles. Retrieved December 15, 2021, from. https://www.sra.org/wp-content/uploads/2020/04/SRA-Fundamental-Principles-R2.pdf
- Aven, T., Ben-Haim, Y., Andersen, H. B., Cox, T., Droguett, E. L., Greenberg, M., Guikema, S., Kroeger, W., Renn, O., Thompson, K. M., & Zio, E. (2018). SRA glossary. Retrieved December 15, 2021, from. https://www.sra.org/risk-analysis-introduction/risk-analysis-glossary/
- Aven, T., & Ylönen, M. (2019). The strong power of standards in the safety and risk fields: A threat to proper developments of these fields? Reliability Engineering & System Safety, 189, 279–286. https://doi.org/10.1016/j.ress.2019.04.035
- Baggett, R. K., & Stout, A. L. (2022). Critical Infrastructure risk analysis and management. In Masys, A.J. (Eds.), Handbook of Security Science, (pp. 3–22). Cham: Springer International Publishing. https://doi.org/10.1007/978-3-319-51761-2_1-1
- Berger, T. B. (2015). Risk assessment competencies of risk management professionals (in Germany). SSRN Electronic Journal. SSRN 2815654. https://doi.org/10.2139/ssrn.2815654
- Birkmann, J., Feldmeyer, D., McMillan, J. M., Solecki, W., Totin, E., Roberts, D., Trisos, C., Jamshed, A., Boyd, E., & Wrathall, D. (2021). Regional clusters of vulnerability show the need for transboundary cooperation. Environmental Research Letters, 16(9), 094052. https://doi.org/10.1088/1748-9326/ac1f43
- Blackwell, J., Tolone, W. J., Lee, S. W., Xiang, W. N., & Marsh, L. (2009). An ontology-based approach to blind spot revelation in critical infrastructure protection planning. In Setola, R., Geretshuber, S. (Eds.), Critical information infrastructure security: Third international workshop, CRITIS 2008, Rome, Italy, October 13-15 2008 (pp. 352–359). Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-03552-4_34
- Bontempo, R. N., Bottom, W. P., & Weber, E. U. (1997). Cross‐cultural differences in risk perception: A model‐based approach. Risk analysis, 17(4), 479–488. https://doi.org/10.1111/j.1539-6924.1997.tb00888.x
- Borghetti, F., Marchionni, G., Gugiatti, E., Ambrosi, C., Czerski, D., & Melzi, C. (2020). Cross border critical infrastructure: A new approach for the protection evaluation. Proceedings of the 30th European Safety and Reliability Conference and the 15th Probabilistic Safety Assessment and Management Conference ESREL 2020 PSAM (Vol. 15ed. pp. 21–26, Venice. June, 2020
- Bossong, R. (2014). The European programme for the protection of critical infrastructures–meta-governing a new security problem? European Security, 23(2), 210–226. https://doi.org/10.1080/09662839.2013.856307
- Bowen, G. A. (2009). Document analysis as a qualitative research method. Qualitative Research Journal, 9(2), 27–40. https://doi.org/10.3316/QRJ0902027
- Burgess, J. P. (2007). Social values and material threat: The European Programme for critical infrastructure protection. International Journal of Critical Infrastructures, 3(3–4), 471–487. https://doi.org/10.1504/IJCIS.2007.014121
- Cambridge on-line Dictionary. (2021). Transnational. Retrieved December 3, 2021, from. https://dictionary.cambridge.org/dictionary/english/transnational
- Center For Homeland Defense and Security. (2020). Homeland Threat Assessment. Retrieved December 2, 2021, from. https://www.hsdl.org/?view&did=845195
- Cianni, M., & Wnuck, D. (1997). Individual growth and team enhancement: Moving toward a new model of career development. Academy of Management Perspectives, 11(1), 105–115. https://doi.org/10.5465/ame.1997.9707100663
- Clemente, D. (2013). Cyber security and global interdependence: What is critical?. Chatham House, Royal Institute of International Affairs.
- Coman, I. M. (2017). Cross-border cyber-attacks and critical infrastructure protection. International Journal of Information Security and Cybercrime (IJISC), 6(2), 47–52. https://doi.org/10.19107/IJISC.2017.02.07
- CORDIS. (2011). European Risk Assessment and Contingency Planning Methodologies for Interconnected energy networks (EURACOM). Retrieved October 29, 2023, from. https://cordis.europa.eu/article/id/89833-increasing-the-security-of-europes-energy-supply
- Dali, A., & Lajtha, C. (2012). ISO 31000 risk management - “The gold standard”. EDPACS, 45(5), 1–8. https://doi.org/10.1080/07366981.2012.682494
- Department of Homeland Security. (2013). NIPP 2013: Partnering for critical infrastructure security and resilience. https://www.dhs.gov/sites/default/files/publications/National-Infrastructure-Protection-Plan-2013-508.pdf
- Department of Homeland Security. (2021). Transnational crime. (7 Dec. 2021). https://www.dhs.gov/keywords/transnational-crime.(Accessed
- Disco, C., & Lintsen, H. W. (1998). Het nijvere verbond. Techniek in Nederland in de twintigste eeuw, 1 https://ris.utwente.nl/ws/portalfiles/portal/134685575/lint011tech01_01.pdf.
- ENISA. (2021). European Union Agency for Cybersecurity. Retrieved April 5, 2021, from. https://www.enisa.europa.eu/
- Equinor. (2013). Publication of the investigation report on the in Amenas terrorist attack. Retrieved March 25, 2024, from. https://www.equinor.com/news/archive/2013/09/12/12SepInAmenasreport
- European Commission. (2016). VITEX 2016 was the first EU-Wide exercise focused on the effects of large-scale failure of critical (electricity) infrastructure across Europe. Retrieved October 29, 2023, from. https://erncip-project.jrc.ec.europa.eu/events/vitex-2016-was-first-eu-wide-exercise-focussed-effects-large-scale-failure-critical
- European Commission. (2019a). Commission notice - reporting guidelines on disaster risk management. Art. 6(1)d of decision No 1313/2013/EU (2019/C 428/07). Official Journal of the European Union 20.12.2019, C 428/8-33.
- European Commission. (2019b). Critical infrastructure protection. Retrieved May 13, 2021, from. https://ec.europa.eu/jrc/en/research-topic/critical-infrastructure-protection
- European Commission. (2022). Opening remarks by commissioner Johansson at the press conference on EU critical infrastructure resilience. Retrieved November 27, 2022, from. https://ec.europa.eu/commission/presscorner/detail/en/SPEECH_22_6265
- European Council. (2008). Directive 2008/114 - Identification and designation of European critical infrastructures and the assessment of the need to improve their protection. Retrieved July 2, 2021, from. https://www.eumonitor.eu/9353000/1/j9vvik7m1c3gyxp/vitgbgipfoqy#p3
- Eusgeld, I., Nan, C., & Dietz, S. (2011). “System-of-systems” approach for interdependent critical infrastructures. Reliability Engineering & System Safety, 96(6), 679–686. https://doi.org/10.1016/j.ress.2010.12.010
- Fairbrother, A., Kapustka, L. A., Williams, B. A., & Glicken, J. (1995). Risk assessment in practice: Success and failure. Human and Ecological Risk Assessment: An International Journal, 1(4), 367–375. https://doi.org/10.1080/10807039509380021
- Fischerkeller, M. P., & Harknett, R. J. (2017). Deterrence is not a credible strategy for cyberspace. Orbis, 61(3), 381–393. https://doi.org/10.1016/j.orbis.2017.05.003
- Fischoff, B. (1984). Acceptable risk. Cambridge University Press.
- Frederick, S. (2005). Cognitive reflection and decision making. Journal of Economic Perspectives, 19(4), 25–42. https://doi.org/10.1257/089533005775196732
- Fritzon, Å., Ljungkvist, K., Boin, A., & Rhinard, M. (2007). Protecting Europe’s critical infrastructures: Problems and prospects. Journal of Contingencies and Crisis Management, 15(1), 30–41. https://doi.org/10.1111/j.1468-5973.2007.00502.x
- Gaiser, L. (2018). European critical infrastructure protection: The need for a regional approach and a cyber constant contact strategy. National Security and the Future, 19(1–2), 45–63.
- Giannopoulos, G., Filippini, R., & Schimmer, M. (2012). Risk assessment methodologies for Critical Infrastructure Protection. Part I: A state of the art. JRC Technical Notes, 1(1), 1–53.
- Gigerenzer, G., & Todd, P. M. (1999). Simple heuristics that make us smart. Oxford University Press.
- Greener, S. (2018). Research limitations: The need for honesty and common sense. Interactive Learning Environments, 26(5), 567–568. https://doi.org/10.1080/10494820.2018.1486785
- Greenhalgh, T., Thorne, S., & Malterud, K. (2018). Time to challenge the spurious hierarchy of systematic over narrative reviews? European Journal of Clinical Investigation, 48(6). https://doi.org/10.1111/eci.12931
- Hammond-Errey, M., & Ray, K. (2021). A new methodology for strategic assessment of transnational threats. Police Practice & Research, 22(1), 40–56. https://doi.org/10.1080/15614263.2019.1699411
- Heino, O., Takala, A., Jukarainen, P., Kalalahti, J., Kekki, T., & Verho, P. (2019). Critical infrastructures: The operational environment in cases of severe disruption. Sustainability, 11(3), 838. https://doi.org/10.3390/su11030838
- Hermansson, H. (2012). Defending the conception of “objective risk”. Risk Analysis: An International Journal, 32(1), 16–24. https://doi.org/10.1111/j.1539-6924.2011.01682.x
- Högselius, P., Hommels, A., Kaijser, A., & Van der Vleuten, E. (Eds). (2013). The making of Europe’s critical infrastructure: Common connections and shared vulnerabilities. Palgrave Macmillan, UK.
- Homeland Security. (n.d.). National infrastructure protection plan - risk management framework. https://www.dhs.gov/xlibrary/assets/NIPP_RiskMgmt.pdf. ( Accessed 12 Sept 2021.
- Houghton, S. M., Simon, M., Aquino, K., & Goldberg, C. B. (2000). No safety in numbers: Persistence of biases and their effects on team risk perception and team decision making. Group & Organization Management, 25(4), 325–353. https://doi.org/10.1177/1059601100254002
- Hutten, J. C., Van Horn, J. E., Uzieblo, K., van der Veeken, F. C., & Bouman, Y. H. (2022). Toward a risk management strategy: A narrative review of methods for translation of risk assessment into risk management. Journal of Forensic Psychology Research and Practice, 22(5), 444–469. https://doi.org/10.1080/24732850.2021.2013359
- Institute of Strategic Risk Management. (2023). ISRM amenas case study. Retrieved March 25, 2024, from. https://www.theisrm.org/en/amenas-case-study
- Jasanoff, S. (1991). Cross-national differences in policy implementation. Evaluation Review, 15(1), 103–119. https://doi.org/10.1177/0193841X9101500106
- Kahneman, D., & Tversky, A. (1982). The psychology of preferences. Scientific American, 246(1), 160–173. https://doi.org/10.1038/scientificamerican0182-160
- Klaver, M. H. A., Luiijf, H. A. M., Nieuwenhuijs, A. H., Cavenne, F., Ulisse, A., & Bridegeman, G. (2008). European risk assessment methodology for critical infrastructures. 2008 First International Conference on Infrastructure Systems and Services: Building Networks for a Brighter Future (INFRA) (pp. 1–5). Rotterdam, Netrherlands: IEEE. https://doi.org/10.1109/infra.2008.5439614.
- Kogan, E. (2014). Expert opinion - trilateral military and energy security co-operation: Reactions from Moscow and Washington, Georgian foundation for strategic and international studies. Retrieved May 31, 2022, from. https://gfsis.org.ge/files/library/opinion-papers/17-expert-opinion-eng.pdf
- Lambrechts, D., & Blomquist, L. B. (2017). Political–security risk in the oil and gas industry: The impact of terrorism on risk management and mitigation. Journal of Risk Research, 20(10), 1320–1337. https://doi.org/10.1080/13669877.2016.1153502
- Lazari, A. (2014). European critical infrastructure protection. Springer International Publishing.
- Lee, R. (2015). Closing the case on the reported 2008 Russian cyber attack on the BTC pipeline June 15, 2015. Retrieved March 26, 2024, from. https://www.sans.org/blog/closing-the-case-on-the-reported-2008-russian-cyber-attack-on-the-btc-pipeline/
- Lidskog, R., Soneryd, L., Uggla, Y., & Irwin, A. (2009). Transboundary risk governance. Routledge.
- Linnerooth-Bayer, J., & Sjostedt, G. (Eds.). (2010). Transboundary risk management. Routledge.
- Luiijf, E., & Klaver, M. (2021). Analysis and lessons identified on critical infrastructures and dependencies from an empirical data set. International Journal of Critical Infrastructure Protection, 35, 100471. https://doi.org/10.1016/j.ijcip.2021.100471
- Lyon, B. K., & Hollcroft, B. (2012). Risk Assessments. Professional Safety, 57(12), 28–34.
- May, P. J., & Koski, C. (2013). Addressing public risks: Extreme events and critical infrastructures. Review of Policy Research, 30(2), 139–159. https://doi.org/10.1111/ropr.12012
- Mousavi, S., & Gigerenzer, G. (2014). Risk, uncertainty, and heuristics. Journal of Business Research, 67(8), 1671–1678. https://doi.org/10.1016/j.jbusres.2014.02.013
- Murata, A., Nakamura, T., & Karwowski, W. (2015). Influence of cognitive biases in distorting decision making and leading to critical unfavorable incidents. Safety, 1(1), 44–58. https://doi.org/10.3390/safety1010044
- Pachur, T., Hertwig, R., & Steinmann, F. (2012). How do people judge risks: Availability heuristic, affect heuristic, or both? Journal of Experimental Psychology: Applied, 18(3), 314. https://doi.org/10.1037/a0028279
- Pidgeon, N., & O’Leary, M. (2000). Man-made disasters: Why technology and organizations (sometimes) fail. Safety Science, 34(1–3), 15–30. https://doi.org/10.1016/S0925-7535(00)00004-7
- Poljanšek, K., Casajus Valles, A., Marin Ferrer, M., De Jager, A., Dottori, F., Galbusera, L., Garcia Puerta, B., Giannopoulos, G., Girgin, S., Hernandez Ceballos, M., Iurlaro, G., Karlos, V., Krausmann, E., Larcher, M., Lequarre, A., Theocharidou, M., Montero Prieto, M., Naumann, G., Necci, A., Salamon, P., Sangiorgi, M., Raposo De M. Do N. E S. De Sotto Mayor, M., Trueba Alonso, C., Tsionis, G., Vogt, J. & Wood, M. (2019). Recommendations for national risk assessment for disaster risk management in EU. Publications Office of the European Union, Luxembourg. https://doi.org/10.2760/147842JRC114650
- Pursiainen, C., & Kytömaa, E. (2023). From European critical infrastructure protection to the resilience of European critical entities: What does it mean? Sustainable and Resilient Infrastructure, 8(sup1), 85–101. https://doi.org/10.1080/23789689.2022.2128562
- Pursiainen, C., & Rød, B. (2021). National disaster risk assessments in Europe. How comparable are they and why? Risk, Hazards & Crisis in Public Policy, 12(2), 194–214. https://doi.org/10.1002/rhc3.12215
- Reid, S. G. (2000). Acceptable risk criteria. Progress in Structural Engineering and Materials, 2(2), 254–262. https://doi.org/10.1002/1528-2716(200004/06)2:2<254:AID-PSE30>3.0.CO;2-K
- Renda, A., & Haemmerli, B. (2010). Protecting critical infrastructure in the EU: CEPS task force report. Retrieved October 22, 2021, from. https://www.ceps.eu/ceps-publications/protecting-critical-infrastructure-eu/,2010
- Rinaldi, S. M., Peerenboom, J. P., & Kelly, T. K. (2001). Identifying, understanding, and analyzing critical infrastructure interdependencies. IEEE Control Systems Magazine, 21(6), 11–25.
- Rød, B., Lange, D., Theocharidou, M., & Pursiainen, C. (2020). From risk management to resilience management in critical infrastructure. Journal of Management in Engineering, 36(4), 04020039. https://doi.org/10.1061/(ASCE)ME.1943-5479.0000795
- Roe, E., & Schulman, P. R. (2018). A reliability & risk framework for the assessment and management of system risks in critical infrastructures with central control rooms. Safety Science, 110, 80–88. https://doi.org/10.1016/j.ssci.2017.09.003
- Rohrmann, B. (2000). Cross-cultural studies on the perception and evaluation of hazards. In: Renn, O., Rohrmann, B. (Eds.), Cross-Cultural Risk Perception. Technology, Risk, and Society (pp. 103–143). Springer, Boston, MA. https://doi.org/10.1007/978-1-4757-4891-8_3
- Sachs, M. (2022). Reflections on executive order 13010. Retrieved October 9, 2022, from. https://mccrary.auburn.edu/work/insights/reflections-on-executive-order-13010/
- Schäferhoff, M., Campe, S., & Kaan, C. (2009). Transnational public-private partnerships in international relations: Making sense of concepts, research frameworks, and results. International Studies Review, 11(3), 451–474. https://doi.org/10.1111/j.1468-2486.2009.00869.x
- Schwenk, C. H. (1986). Information, cognitive biases, and commitment to a course of action. Academy of Management Review, 11(2), 298–310. https://doi.org/10.2307/258461
- Shefrin, H. (2015). How psychological pitfalls generated the global financial crisis. In Laurence B. S (Ed.), The Routledge companion to strategic risk management (pp. 289–315). Routledge.
- Skagerlund, K., Forsblad, M., Slovic, P., & Västfjäll, D. (2020). The affect heuristic and risk perception–stability across elicitation methods and individual cognitive abilities. Frontiers in Psychology, 11, 970. https://doi.org/10.3389/fpsyg.2020.00970
- Skogstad, G. (2003). Legitimacy and/or policy effectiveness?: Network governance and GMO regulation in the European Union. Journal of European Public Policy, 10(3), 321–338. https://doi.org/10.1080/1350176032000085333
- Slovic, P. (2000). The Perception of Risk. www.routledge.com
- Slovic, P. (2020). Risk perception and risk analysis in a hyperpartisan and virtuously violent world. Risk analysis, 40(S1), 2231–2239. https://doi.org/10.1111/risa.13606
- Slovic, P., Baruch Fischhoff, B., & Lichtenstein, S. (1979). Rating the Risks. Environment: Science and Policy for Sustainable Development, 21(3), 14–39. https://doi.org/10.1080/00139157.1979.9933091
- Slovic, P., Finucane, M. L., Peters, E., & MacGregor, D. G. (2004). Risk as analysis and risk as feelings: Some thoughts about affect, reason, risk, and rationality. Risk Analysis, 24(2), 311–322. https://doi.org/10.1111/j.0272-4332.2004.00433.x
- Slovic, P., Finucane, M. L., Peters, E., & MacGregor, D. G. (2007). The affect heuristic. European Journal of Operational Research, 177(3), 1333–1352. https://doi.org/10.1016/j.ejor.2005.04.006
- Slovic, P., Fischhoff, B., & Lichtenstein, S. (1981). Rating the Risks. In Y. Y. Haimes (Ed.), Risk/Benefit analysis in water resources planning and management (pp. 193–217). Springer. https://doi.org/10.1007/978-1-4899-2168-0_17
- Slovic, P., Fischhoff, B., & Lichtenstein, S. (1982). Why study risk perception? Risk analysis, 2(2), 83–93. https://doi.org/10.1111/j.1539-6924.1982.tb01369.x
- Slovic, P., Layman, M., & Flynn, J. H. (1991). Risk perception, trust, and nuclear waste: Lessons from Yucca Mountain. Environment: Science and Policy for Sustainable Development, 33(3), 6–30. https://doi.org/10.1080/00139157.1991.9931375
- Sofaer, A. D., & Goodman, S. E. (2001). Cyber crime and security. The transnational dimension. In A.D. Sofaer & S.E. Goodman (Eds), The Transnational Dimension of Cyber-Crime and Terrorism, (pp. 1–34). Hoover Institution Press. https://onlinebooks.library.upenn.edu/webbin/metabook?id=hoovercyber.
- Sonesson, T. R., Johansson, J., & Cedergren, A. (2021). Governance and interdependencies of critical infrastructures: Exploring mechanisms for cross-sector resilience. Safety Science, 142, 105383. https://doi.org/10.1016/j.ssci.2021.105383
- Starr, S. & Cornell, S. (2005). The baku-tbilisi-ceyhan pipeline: Oil window to the west. Central Asia-Caucasus Institute & Silk Road Studies Program. (Accessed 20 September. https://www.silkroadstudies.org/resources/pdf/Monographs/2005_01_MONO_Starr-Cornell_BTC-Pipeline.pdf
- Statoil. (2013). The in Amenas report, report on the investigation into the terrorist attack on in Amenas. Prepared for statoil ASA’s board of directors. Retrieved March 25, 2024, from. https://www.equinor.com/news/archive/2013/09/12/downloads/In%20Amenas%20report.pdf
- Stockton, P., & Roberts, P. (2008). Findings from the Forum on Homeland Security after the Bush Administration: Next steps in building unity of effort. Homeland Security Affairs, 4(2). Article 4 (June 2008). https://www.hsaj.org/articles/121
- Sunstein, C. R. (2005). Precautions against what? the availability heuristic and cross-cultural risk perception. SSRN Electronic Journal, 57, 75. https://doi.org/10.2139/ssrn.578303
- Theocharidou, M., & Giannopoulos, G. (2015). Risk assessment methodologies for critical infrastructure protection. Part II: A new approach. Scientific and Technical Research Reports, Report EUR 27332 EN. https://doi.org/10.2788/621843
- Toplak, M. E., West, R. F., & Stanovich, K. E. (2011). The cognitive reflection test as a predictor of performance on heuristics-and-biases tasks. Memory & Cognition, 39(7), 1275–1289. https://doi.org/10.3758/s13421-011-0104-1
- Trumbo, C., Lueck, M., Marlatt, H., & Peek, L. (2011). The effect of proximity to Hurricanes Katrina and Rita on subsequent hurricane outlook and optimistic bias. Risk Analysis: An International Journal, 31(12), 1907–1918. https://doi.org/10.1111/j.1539-6924.2011.01633.x
- Tversky, A., & Kahneman, D. (1973). Availability: A heuristic for judging frequency and probability. Cognitive Psychology, 5(2), 207–232. https://doi.org/10.1016/0010-0285(73)90033-9
- Tversky, A., & Kahneman, D. (1974). Judgment under uncertainty: Heuristics and biases: Biases in judgments reveal some heuristics of thinking under uncertainty. Science, 185(4157), 1124–1131. https://doi.org/10.1126/science.185.4157.1124
- Ulusan, A., Ergun, O., & He, Z. (2018). Restoration of services in disrupted infrastructure systems: A network science approach. Public Library of Science ONE, 13(2), e0192272. https://doi.org/10.1371/journal.pone.0192272
- US Congress. (2021). Public law 107-56 uniting and strengthening America by providing appropriate tools required to intercept and obstruct terrorism (USA Patriot Act) Act of 2001. Retrieved October 23, 2021, from. https://www.congress.gov/107/plaws/publ56/PLAW-107publ56.pdf
- US Election Assistance Commission. (2017). History of critical Infrastructure designation. Retrieved October 23, 2021, from. https://www.eac.gov/ci-scoop-history-of-critical-infrastructure-designation
- Van der Vleuten, E., & Disco, C. (2004). Water wizards: Reshaping wet nature and society. History and Technology, 20(3), 291–309. https://doi.org/10.1080/0734151042000287014
- Van der Vleuten, E., & Lagendijk, V. (2010a). Interpreting transnational infrastructure vulnerability: European blackout and the historical dynamics of transnational electricity governance. Energy Policy, 38(4), 2053–2062. https://doi.org/10.1016/j.enpol.2009.11.030
- Van der Vleuten, E., & Lagendijk, V. (2010b). Transnational infrastructure vulnerability: The historical shaping of the 2006 European “blackout”. Energy Policy, 38(4), 2042–2052. https://doi.org/10.1016/j.enpol.2009.11.047
- Van Eeten, M., Nieuwenhuijs, A., Luiijf, E., Klaver, M., & Cruz, E. (2011). The state and the threat of cascading failure across critical infrastructures: The implications of empirical evidence from media incident reports. Public Administration, 89(2), 381–400. https://doi.org/10.1111/j.1467-9299.2011.01926.x
- Van Schaik, P., Renaud, K., Wilson, C., Jansen, J., & Onibokun, J. (2020). Risk as affect: The affect heuristic in cybersecurity. Computers & Security, 90, 101651. https://doi.org/10.1016/j.cose.2019.101651
- Varma, R., & Varma, D. R. (2005). The Bhopal disaster of 1984. Bulletin of Science, Technology & Society, 25(1), 37–45. https://doi.org/10.1177/0270467604273822
- Veland, H., & Aven, T. (2015). Improving the risk assessments of critical operations to better reflect uncertainties and the unforeseen. Safety Science, 79, 206–212. https://doi.org/10.1016/j.ssci.2015.06.012
- Vertovec, S. (1999). Conceiving and researching transnationalism. Ethnic and Racial Studies, 22(2), 447–462. https://doi.org/10.1080/014198799329558
- Weber, E. U., & Hsee, C. (1998). Cross-cultural differences in risk perception, but cross-cultural similarities in attitudes towards perceived risk. Management science, 44(9), 1205–1217. https://doi.org/10.1287/mnsc.44.9.1205
- White House. (1998). Presidential decision directive NSC-63: Critical infrastructure protection. Retrieved October 22, 2021, from. https://irp.fas.org/offdocs/pdd/pdd-63.htm
- Yildiz, A. E., Dikmen, I., & Birgonul, M. T. (2014). Using expert opinion for risk assessment: A case study of a construction project utilizing a risk mapping tool. Procedia-Social and Behavioral Sciences, 119, 519–528. https://doi.org/10.1016/j.sbspro.2014.03.058
- Yu, Y., Chan, A. P., Chen, C., & Darko, A. (2018). Critical risk factors of transnational public–private partnership projects: Literature review. Journal of Infrastructure Systems, 24(1), 04017042. https://doi.org/10.1061/(ASCE)IS.1943-555X.0000405
- Yusta, J. M., Correa, G. J., & Lacal-Arántegui, R. (2011). Methodologies and applications for critical infrastructure protection: State-of-the-art. Energy Policy, 39(10), 6100–6119. https://doi.org/10.1016/j.enpol.2011.07.010
- Zio, E. (2016). Challenges in the vulnerability and risk analysis of critical infrastructures. Reliability Engineering & System Safety, 152, 137–150. https://doi.org/10.1016/j.ress.2016.02.009